
Design and Development of a Hospital Biometric Data Management System
Smith Orode Otuagoma 1![]()
![]() ,
Ikponmwosa Oghogho 2
,
Ikponmwosa Oghogho 2![]()
![]() ,
Ebimene Ezekiel Ebisine 3
,
Ebimene Ezekiel Ebisine 3![]()
![]() ,
Okieke Ufuoma Jeffrey 3
,
Okieke Ufuoma Jeffrey 3![]()
![]() ,
Uzonna Gabriel Anamonye 4
,
Uzonna Gabriel Anamonye 4![]()
![]() ,
Oyubu Akpovi Oyubu 4
,
Oyubu Akpovi Oyubu 4![]()
![]() ,
Anthony Onoharigho Okpare 4
,
Anthony Onoharigho Okpare 4![]()
![]() ,
Ogheneakpobo Jonathan Eyenubo
4
,
Ogheneakpobo Jonathan Eyenubo
4![]()
![]() ,
Gabriel Ilori Efenedo 1
,
Gabriel Ilori Efenedo 1![]()
![]() ,
Kazeem Ufuoma Okpeki 1
,
Kazeem Ufuoma Okpeki 1![]() , Franklin F. Emefile 5
, Franklin F. Emefile 5
1 Senior
Lecturer, Department of Electrical and Electronic Engineering, Delta
State University Abraka, Oleh Campus, Delta State,
Nigeria
2 Associate Professor, Department of Electrical and Electronic
Engineering, Delta State University, Abraka, Oleh
Campus, Delta State, Nigeria
3 Lecturer II, Electrical and Electronics Engineering Department, Delta
State University Abraka, Oleh campus, Delta State,
Nigeria
4 Lecturer I, Department of Electrical and Electronics Engineering
Delta State University Abraka, Oleh campus, Delta State,
Nigeria
5 Graduate Student, Department of Electrical and Electronic
Engineering, Delta State University, Abraka, Oleh
Campus, Delta State, Nigeria
|
|
ABSTRACT |
||
|
The need to drastically reduce the delay faced by patients before they receive treatment in the University Clinic and the need to reduce the occurrence of medical mistakes due to patient’s misidentification led to this work which aimed at developing a hospital biometric data management system. Java was the programming language of choice and Netbeans was the Integrated Development Environment (IDE) used to design the Graphical User Interphase (GUI) and write codes. For the backend database, MySQL was used for demonstration purposes. The analytical diagrams were drawn using VioletUMLEdit. The Griaule Fingerprint Software Development Kit (SDK) was used to implement the fingerprint capture, enrollment, identification and verification features of the software. The tests and
results obtained showed that with this hospital management system, the time
taken to retrieve patient’s record has been reduced from several minutes to
less than five seconds thereby eliminating the delay experienced by patients
during search of their records. The problem of medical mistakes due to
patient’s misidentification was also addressed by the biometric feature of
the management system. |
|||
|
Received 02 December 2022 Accepted 01 January 2023 Published 16 February 2023 Corresponding Author Ikponmwosa Oghogho, oghoghoik@gmail.com DOI 10.29121/IJOEST.v7.i1.2023.464 Funding: This research
received no specific grant from any funding agency in the public, commercial,
or not-for-profit sectors. Copyright: © 2023 The
Author(s). This work is licensed under a Creative Commons
Attribution 4.0 International License. With the
license CC-BY, authors retain the copyright, allowing anyone to download,
reuse, re-print, modify, distribute, and/or copy their contribution. The work
must be properly attributed to its author.
|
|||
|
Keywords: Hospital
Biometric, Data Management System, Biometric Feature |
|||
1. INTRODUCTION
The rapid growth in Information and Communication Technologies (ICTs) has strongly impacted human activities globally including the service delivery models of many organizations with respect to healthcare, businesses, education, governance, etc. Oghogho & Ezomo (2013). As more and more industries embrace the features of ICTs to enhance the way they serve their customers, the healthcare industry is largely affected because effective or ineffective customer service can lead to permanent impairment or even death.
E-Hospital Management Systems provide the benefits of
streamlined operations, enhanced administration and control, superior patient
care, strict cost control and improved profitability. Balaraman & Kosalram (2013)
Today more hospitals and healthcare systems have migrated to electronic health records, and more health information exchanges are built to coordinate care across various hospitals’ networks. Because of this rapid migration, concerns have been raised about how to effectively manage data integrity to ensure it is kept free from corruption, modification, or unauthorized access. The multiple access to healthcare Electronic Health Records (EHR) and the transition of data across Health Information Exchange (HIEs) open the door to data corruption. In most other industries, data integrity is just as important, but corruption errors can be rectified, and mistakes fixed. However, this can mean the difference between life and death within the healthcare industry.
One of the ways to maintain data integrity is to implement a consistence approach to matching patients with their data across the Health Information Exchanges. That is, as patients’ data transit from one healthcare centre’s network to another, there must be a mechanism to identify a particular patient data before modification can be made and treatment given. Also, personnel attempting to access patients’ health records must provide reliable authentication.
The traditional mechanism of applications requiring the use of a password, pin, ID card, key, or a combination of these might not be too safe today due to increasing global violence and terrorism. In addition, in today’s world where larger amounts of sensitive personal information are stored in databases and accessed in many ways, new methods of identification that significantly reduce the probability of fraud are becoming essential. In addition to this, the Health Insurance Portability and Accountability Act (HIPAA Act) imposes stringent new requirements to protect patient’s privacy and the confidentiality of their information. To provide a reliable way of authenticating hospital personnel, a new solution that utilizes features that are unique to individuals must be implemented. This is the major reason why the health care industry is embracing the biometric technology.
Biometrics can be defined as the development of statistical and mathematical methods applicable to data analysis in the biological sciences Mason et al. (2020). True biometrics systems began to emerge in the late 1900's. This coincided with the emergence of computer systems hence the field experienced an explosion of activities which has made biometrics a part of our normal everyday application today.
The protection of data especially that of patient’s medical records, is of utmost importance. This is implemented by system developers using various methods of authentication. Biometric authentication is synonymous with the way humans identify one another. Biometric systems rely on measurable physiological or behavioral characteristics that can be utilized to identify or verify the identity of an individual. Ahmad et al. (2010)
Ahmad et al. (2012), clarified that physiological-based biometric systems include fingerprints, retina, iris, hand geometry, hand vein etc. These features are consistent on an individual for long periods of time. Unlike the authentication process that involves something one has that can be lost, duplicated, shared, or even altered these features are usually unalterable without causing trauma to the individual.
The versatility of biometric systems is that they not only use physiological human traits but also use the complex and deeply wired behavioral characteristics of humans. These behavioral characteristics are traits that are learned or acquired which later stabilize over a period of time, for example, voice recognition, keystroke dynamics, signature verification etc.
Humans happen to have a built-in "identity card" that differentiates them from one another. This is the fingerprint. No two individuals have exactly the same pattern of fingerprints. The tiny ridges and "valleys" that form the pattern of an individual's fingerprint is an advantageous feature of adaptation. Even though two fingerprints might look identical at first glance, it would not take long before an experienced analyst or an advance piece of software detect the difference in the patterns. This is the basic idea of fingerprint analysis.
Fingerprint scanners have two jobs: get the image of a fingerprint and determine if the pattern of ridges and valleys of the image matches the pattern of ridges and valleys in pre-scanned fingerprints. There are two main methods of getting the image of fingerprints, and they are optical scanning and capacitance scanning. Both methods get about the same sort of image, but they go about it in completely different ways.
Initially, biometric systems were developed to aid Law Enforcement Agency, like the Police, to identify criminals. However, due to recent advances in biometric systems, increased power and efficiency of computing devices and recent outburst of information security threats, biometric systems have wandered into the physical and logical access control domains.
Biometric systems have a wide range of applications making reference to the Malaysian identity card known as ‘MyKad’ as national initiative deployed by the Malaysian government that incorporates fingerprint biometric to identify a person’s identity and citizenship. In the United States, physical entrances into its nuclear power plants are only granted based on hand geometric recognition. In addition, iris scanning has also been deployed at the United States Office of Legislative Counsel to ensure the confidentiality of its files and documents.
According to Ahmad et al. (2011) although biometric systems have a wide range of applications, different biometric systems basically differ in their underlying technologies, complexities and performances; hence they have their strengths and limitations. Therefore, a detailed study on the trade-offs and risk management is imperative in information security policy and decision making prior to and during the deployment of a biometric solution or other solutions as the case may be.
Data can simply be said to be an organizational asset. In ancient times, the big drivers of the need to keep detailed records were trade and taxation. Basically, people needed to keep track of who owed them, how much and for what. This meant that people not only needed a way of recording, but people also needed a way of retrieving it and updating it. Due to these needs, the development of double entry bookkeeping emerged. With this record keeping was settled, however, retrieving data from numerous books remained a tedious activity. In paper-based systems, indexes were developed to ease and speed up data retrieval process.
The production of reports from stored data was manual, time consuming and error prone, hence major financial reports were scheduled monthly and yearly. On demand reports were completely impossible, and the end of the month and end of the year were usually the busiest periods in the accounts section of an organization.
The development of the computer was a huge step into the digital age as other financial companies began using the computer because data could now be processed with speed, and it was less prone to error. Also reports that were more up to date could be produced. Hard drives and operating systems were introduced, and this allowed multiple users and multiple programs to be active, thereby, removing the tight scheduling due to single process machines. This made it possible to access individual records directly in real time.
Although the present level of database technology ensures that vital information and records in an organization can be effectively stored and quickly retrieved when needed, it is regrettable that many clinics and hospitals in Nigeria, where the storage and retrieval of patients’ record is highly important, still use old models of bookkeeping to store patients’ records. Considerable time is spent in retrieving a patient’s record from the stack of records. It is believed that with the right implementation of modern database technology and software, the time spent in retrieving patients’ records can be considerably reduced to its lowest minimum, hopefully to milliseconds. Today, several organizations are battling issues of fraud, cyber-attacks, and data theft, hence their need to use biometrics to help them protect patient’s data while also safeguarding their reputations. This work is therefore intended to design and develop a robust hospital biometric data management system using Delta State University clinic as a case study so as to protect the privacy of patients’ records by ensuring that only authorized staff can access the data, and to digitize the task of retrieving a patient’s record by deploying database technology and biometrics.
2. REVIEW OF PAST WORK
Identification and verification have long been accomplished by showing 'something one has', such as a license or a passport. Sometimes it also requires 'something one knows', such as a password or a PIN. As we live in a time when we need more secure and accurate measures, we begin to look at using 'something one is' which is biometrics. Mason et al. (2020) investigated biometric system alongside the process involved in authentication. In the study, periocular biometrics was used. This approach was integrated with the healthcare system thereby providing an advanced means of securely identifying patients. They proposed a technique to identify humans in hospitals and other healthcare facilities by fusing of periocular biometrics and the electronic master patient index in healthcare information systems. Priya et al. (2016) presented a method to capture, match and verify individuals using feature extraction form the iris and the palm print. The extracted features were compared with database images to obtain matching score which then determined whether the individual is authorized or denied access. In this work, fingerprint biometrics is deployed along with database technology to provide an hospital biometric data management system for Dalta State University, Abraka, Oleh Campus Clinic.
3. MATERIALS AND METHODS
The
Hospital Biometric Data Management System required software that will enable authorized hospital
staff store and/or access patients’ information. The hospital staff is
basically made up of the doctor, the nurses, the record officer, and the
pharmacist. Among these various staff, the pharmacist is the only one who does
not have the privilege to edit a patient’s records. All the pharmacists can do
is access the prescriptions administered by the doctor and give the patient the
required drug.
At
first, the entire hospital staff will be registered into the system, providing
among other things their fingerprints. These fingerprints will be stored in the
database and will be used for authenticating any person trying to gain access
into the system. This mechanism of authentication will beef up the security of
the system, thereby protecting vital patients’ data according to the HIPAA.
During the registration of staff, it is very important to state the position of
the particular staff (whether a doctor, nurse, record officer or pharmacist) as
this will inform the software whether that particular staff can store and
access patient’s data or just access it.
To
use the software, the staff must be authenticated by the system. The system
takes the person’s fingerprint and compares it with pre-scanned fingerprints in
the database. If the fingerprint matches one in the database, the system
proceeds to ask for the person’s secret password. For the person to gain access
into the system, the password the person provides must match the password that
corresponds with the fingerprint in the database. This means that the database
must contain a staff’s ID, name, password, fingerprint, position, and other
data.
A
platform is provided on the software for only one administrator for the sake of
simplicity and low cost. Vested on the administrator is the power to register
staff and also to delete staff in the case of firing a staff or a staff been
deceased or retired.
The
system administrator is added by a software expert who has the privilege to
access the database directly. On the event of someone trying to log into the
system, the system first determines whether the person is the admin or a
regular staff. If the person is verified to be the admin, the software opens a
page different from the one opened for a regular staff because the admin does
not have the privilege to add or view patient’s data but can only add or delete
staff. Therefore, the software displays a page that basically has two buttons:
ADD PERSONNEL and DELETE PERSONNEL. Clicking the ADD PERSONNEL button opens a form
to collect the personnel’s data. The form has the same set of three buttons as
the form for collecting new patient’s data: CLEAR FORM, SUBMIT and CANCEL.
If
the admin clicks the DELETE PERSONNEL button, a table is displayed. The table
contains all the personnel that have been registered. Within this table is the
option to delete or edit the details of a particular staff.
In
this Hospital Management Software, there are five types of users namely: the
record officer, the nurse, the doctor, the pharmacist, and the admin. Each user
has specific demands of the software.
The
record officer uses the software to add new patients, delete patient’s records,
edit personal data, retrieve patient’s record, and edit patient’s record. The
nurse, on the other hand, uses the software to edit personal data, retrieve
patient’s record and edit patient’s record. The admin uses the software to add
personnel, delete personnel and edit personal data. The doctor uses the
software to add patient, delete patient, edit patient’s records, edit personal data,
and view patient’s record whereas the pharmacist can only view patient’s data
and edit personal data.
When
a patient comes to the clinic, the first staff the patient encounters is the
record officer. The record officer ascertains whether the patient is a new or
an old patient. If the patient is new, the record officer proceeds to get the
patient’s details. Details like surname, first name, sex, age, occupation,
local government area, academic session, next of kin, address, and fingerprint.
Upon
collecting these data from the patient, the record officer assigns to a patient
a reference number (coded form of identity) and gives the patient a clinic card.
The record officer and other staff use the reference number to search for the
patient’s hospital records.
After
the record officer has stored the patient’s data, he creates a Treatment card
for the patient. The treatment card normally contains a form on which some of
the patient’s data are entered (data like name, address, age, and sex) and a
table with two columns- Date and Notes. It is in these columns the doctor fills
in the patient’s symptoms, the doctor’s assessment, prescription, and the date
of consultation. The record officer attaches a passport photograph of the
patient on the treatment card and transfers this treatment card to a nurse. The
nurse takes the vital signs of the patient. Vital signs like blood pressure
(BP), pulse rate, temperature, weight, and height.
The
analysis for the Hospital Management System was done using the Unified Modeling Language (UML). The software used to draw the
various UML diagrams is VioletUMLEdit. VioletUMLEdit is free software developed for programmers to
aid in the analysis stage of software development. The analysis of the Hospital
Management System was done using information gathered from the day to day
running operations of the University clinic. The use case diagram of the system
is shown in Figure 1 below:
Figure 1
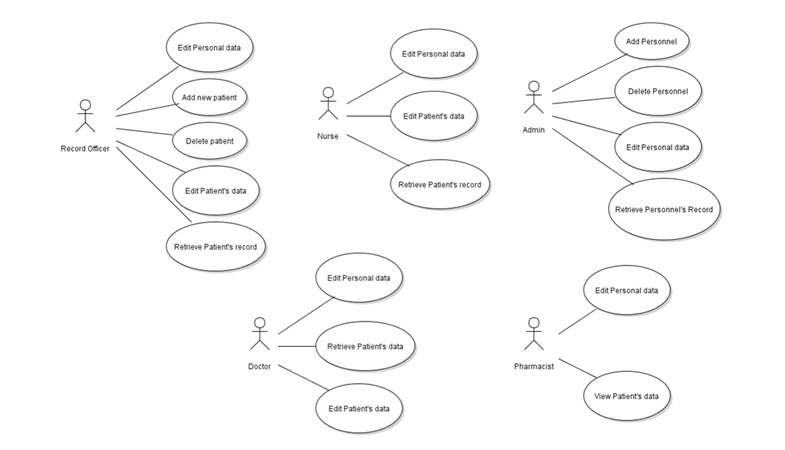
|
Figure 1 Use Case Diagrams of the System |
The
UML enables software engineers to model the system structure via class
diagrams. A class is modelled in UML with a three compartments rectangle; the
top compartment contains the name of the class in bold typeface, the middle
compartments contain the attributes of the class (that is, the instance
variables of the class) and the bottom compartment holds the behaviours of the
class (that is, the methods of the class).
The
hospital management system contains the following classes: Staff, Patient, Database
Connection, Hospital Database, Login Form, Staff Home, Admin Home. Edit Staff Details
Form, All Patients, New Patient Form, Patient Details, New Staff Form, All Staff
and Treatment Card.
In
UML, instance variables are modelled as attributes and are contained in the
second compartment of the class diagrams while methods are modelled as
behaviours and are contained in the third compartment of the class diagrams as
shown in Figure 2 and Figure 3 respectively.
Figure 2

|
Figure 2 Class Diagrams of Some Classes in the System |
Figure 3

|
Figure 3 Class Diagrams of Some Classes in the System |
In
Java, objects are created from classes. Objects from the moment they are
created execute some programming steps to accomplish their overall tasks. In
UML, activity diagrams show the workflow (i.e., sequence of events) of objects.
In Figure 4, Figure 5, Figure 6, Figure 7, Figure 8 are shown the activity
diagrams of the various classes in the Hospital Management System.
Figure 4

|
Figure 4 Activity Diagram of the Login Form |
Figure 5

|
Figure 5 Activity Diagram of New Patient Form |
Figure 6

|
Figure 6 Activity Diagram of New Staff Form |
Figure 7

|
Figure 7 Activity Diagram of Admin Home |
Figure 8

|
Figure 8 Activity Diagram of Staff Home |
In
the development of the Hospital Management System, two hardware components and
four software components were used. The hardware components are Laptop and
Fingerprint Reader (ZK9000) while the software components are Netbeans, MySQL, Phpmyadmin,
Griaule SDK and VioletUMLEdit.
The
Hospital Management System was developed with a laptop (HP635) on which Java
Virtual Machine (JVM) was installed. The JVM enables the laptop to run Java
programs. The fingerprint reader (ZK9000) was integrated with the Hospital
Management System. It takes the fingerprint of the users of the software. The
machine has a USB cable with which it can be connected to the laptop or
computer running the software. Netbeans (a Java IDE)
was installed on the laptop and used to create the forms in the Hospital
Management System. It was also used to write the required java codes for the
respective classes or modules as it has various features (color
syntaxing, auto-suggestion, blocking of codes, etc) that
it uses to make writing codes less tedious and make debugging faster.
MySQL
was used as the database for storing the records of patients and other data.
MySQL was preferred to other databases because it is free, and it is an
open-source database system used by most developers. The MySQL database was
connected to the java program through the necessary lines of codes written for
that purpose.
The
Griaule SDK is the Software Development Kit. It is a library of classes,
methods and other programming tools programmers use to develop software hence
it was used to integrate the hospital management system with the fingerprint
reader. The VioletUMLEdit (a free software used for
drawing the diagrams in the UML) was used to draw all the class diagrams and the
activity diagrams of all the classes (modules).
The
Hospital Database is the database module that holds the records of patients and
the credentials of staff used in this system. The Hospital Database contains
three tables- patients, staff, and treatment. The patients table holds
patients’ records, the staff table holds staffs’ credentials and the treatment
table stores treatment schedules for each patient as shown in Figure 9, Figure 10, Figure 11.
Figure 9
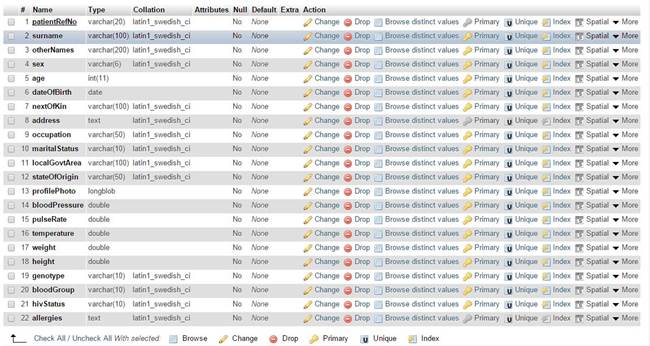
|
Figure 9 Screen Shot of Patient’s Table in the Hospital Database Module |
Figure 10
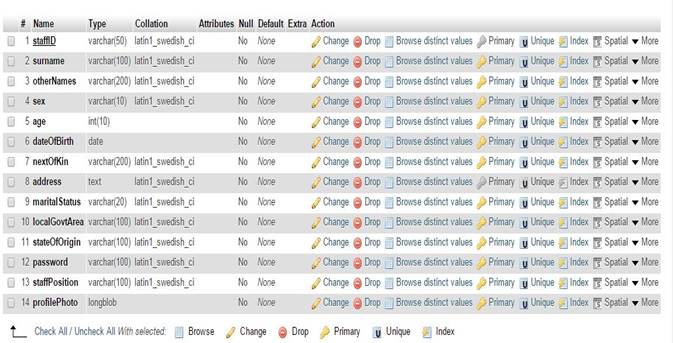
|
Figure 10 Screen Shot of Staff Table in the Hospital Database Module |
Figure 11
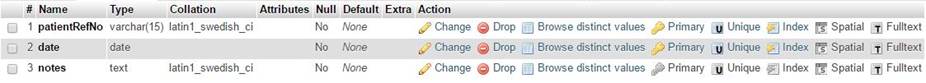
|
Figure 11 Screen Shot of Treatment Table in the Hospital Database Module |
The complete Class diagram of the whole Hospital Management System is shown in Figure 12.
Figure 12

|
Figure 12 Complete Class Diagram of the Whole Hospital Management System |
There
are two basic retrieval modes in the system, they are: Primary key retrieval
mode and fingerprint retrieval mode. In the primary key retrieval mode, the
software searches for a patient’s record or staff record by using a patient
reference number or staff identification number respectively. This mode was
implemented by providing a JTextField and JButton components. The user of the software, for instance,
a staff trying to search a patient’s record will type in the patient reference
number into the JTextField and press the JButton component. On clicking the JButton,
the event is handled by grabbing the patient’s reference number and performing
a SELECT query to the database.
In
the fingerprint retrieval mode, a patient’s record is retrieved from the system
database by providing the patient’s fingerprint. Here, the idea is that once
the fingerprint reader captures one’s fingerprint, it has four options- enroll, verify, identify, and extract template. These four
options are implemented by providing four JButton
components. Fingerprint SDK Java application overview is shown in Figure 13
Figure 13
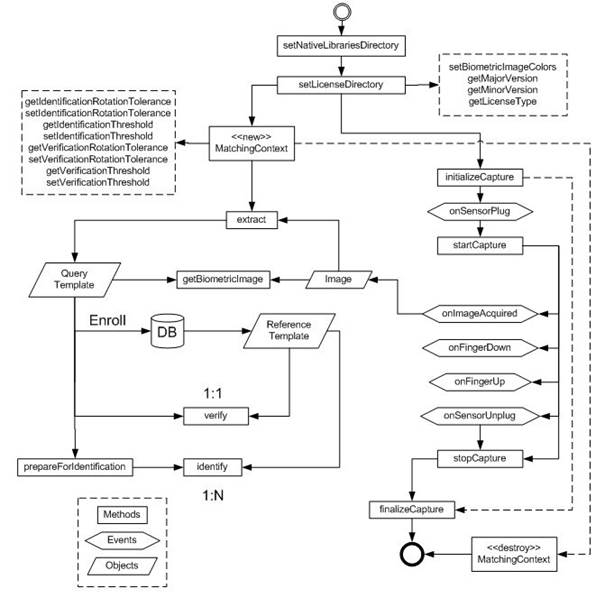
|
Figure 13 Fingerprint SDK Java Application Overview |
4. Tests, Results and Discussion
Tests were conducted on the implemented hospital management system to check the results of the written codes and the performance of the software. The test of this software was carried out in the university clinic using sample data of some of the clinic’s patients.
The intentions of the test carried out are: (i) to record the new time taken to store a new patient’s data into the new system, (ii) to record the new time taken to retrieve a patient’s record from the database system both with the fingerprint and the patient reference number, (iii) to check the visual results of the software Graphic User Interface (GUI) codes (iv) to check if the system is 100% percent accurate in retrieving a particular patient’s record and not mistakenly another’s.
The tests carried out are as follows: (i) GUI Display Test (ii) Patient Registration Test (iii) Record Retrieval Test and (iv) Retrieval Accuracy Test.
Samples of some visual results of some modules of the software are shown Figure 14, Figure 15, Figure 16
Figure 14
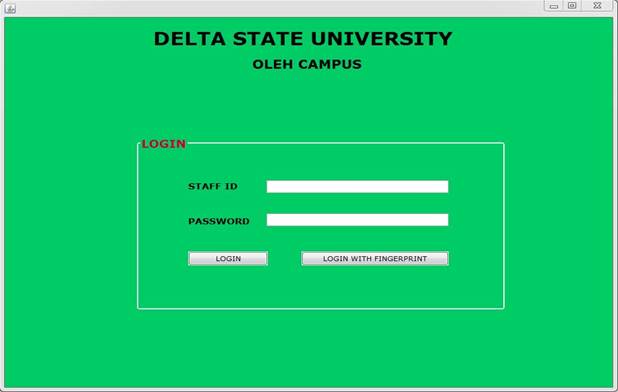
|
Figure 14 Login Form |
Figure 15
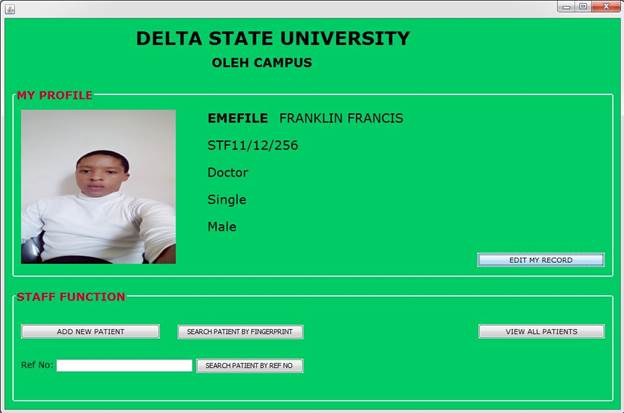
|
Figure 15 Staff Home |
Figure 16
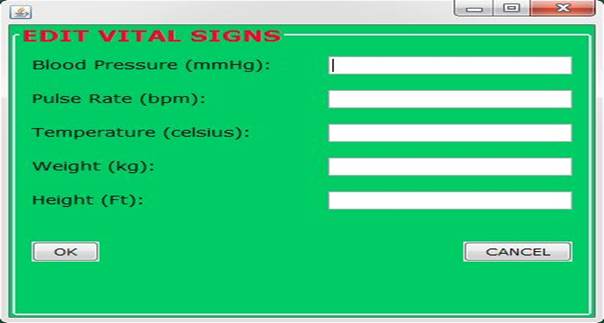
|
Figure 16 Edit Vital Signs |
The Patient registration test was carried out to find out the amount of time it will take to register a new patient with the software compared to doing so manually. The results are shown in Table 1
Table 1
|
Table 1 Patient Registration Test |
||
|
Expertise |
Time taken without software |
Time taken with software |
|
Average computer user |
≥7mins |
≤5mins |
|
Good computer user |
≥7mins |
≤2mins |
Table 1 showed that without the use of the software the process of patient registration usually takes seven minutes or above. However, with the use of the software, the time taken depends on the expertise of the staff.
This record retrieval test was carried out to find out the amount of time it will take to retrieve a particular patient’s record with the software compared to doing so manually. The results are shown in Table 2 below:
Table 2
|
Table 2 Record Retrieval Test |
||
|
Expertise |
Time taken without software (Manually) |
Time taken with software |
|
Average computer user |
≥5mins |
≤5secs |
|
Good computer user |
≥5mins |
≤5secs |
Table 2 showed that the amount of time taken to retrieve a patient’s record is tremendously reduced by the software.
The retrieval accuracy test was carried out to find out the accuracy of the software in retrieving the right patient’s records. To perform this test the software was used to search numerous patients’ record with their patient reference numbers and the system gave accurate results. The software has 100% retrieval accuracy.
5. Conclusion and Recommendation
The Hospital Biometric Data Management System presented here has obviously reduced the time it takes to register a new patient, retrieve patient’s records, and has improved the accuracy of retrieval of patient and staff data. The first two benefits practically helped in reducing the delay patients face in the clinic and help them to start receiving treatment as soon as possible. The third benefit helped to reduce the problem of medical mistakes; especially medical mistakes due to patient misidentification.
The hospital management system was developed with a two-mode retrieval operation- retrieval based on patient’s reference number and patient’s fingerprint. Both retrieval modes query the database for data using either the patient’s reference number or the patient’s fingerprint. Hence, it was necessary that system has a central data house from where patient’s data can be fetched. And each patient’s data has been associated with the patient’s reference number and the patient’s fingerprint.
The system was built to be compatible with major fingerprint readers. This was made possible by using Griaule Fingerprint SDK. It was necessary that the system runs with major fingerprint readers so that the university clinic does not have to worry about which fingerprint reader to use with the system.
Future development of this system should focus on the following: (i) development of a mobile application for this system so that the patient can be reminded about their prescription in whatever the patient’s location, their appointments with the doctor and other relevant details the patient needs to be reminded about (ii) development of a version of this system that will have internet compatibility so that patients’ records can be securely transferred between various medical centres (iii) Development of a version that will add the feature of billing in the hospital management system, so that patients can be billed through the software, and can also pay by using their credit cards.
CONFLICT OF INTERESTS
None.
ACKNOWLEDGMENTS
None.
REFERENCES
Ahmad, S. M. S., Ali, B. M., & Adnan, W. A. W. (2012). Applications as Access Control Tools of Information Security. International Journal of Innovative Computing Information and Control, 8(11), 7983–7999.
Ahmad, S. M. S., Shakil, A., Faudzi, M. A., & Anwar, R. M. (2010). Analysis of “Goats” within User Population of an Offline Signature Biometrics. In Proceedings of the of the 10th International Conference of Information Science. Signal Processing and Applications, 765–769. https://doi.org/10.1109/ISSPA.2010.5605415.
Balaraman, P., & Kosalram, K. (2013). E-Hospital Management and Hospital Information Systems- Changing Trends. International Journal of Information Engineering and Electronic Business, 5(1), 50–58. https://doi.org/10.5815/ijieeb.2013.01.06.
Mason, J., Dave, R., Chatterjee, P., Graham-Allen, I., Esterline, A., & Roy, K. (2020). An Investigation of Biometric Authentication in the Healthcare Environment. Array. Elsevier, 8. https://doi.org/10.1016/j.array.2020.100042.
Oghogho, I., & Ezomo, P. I. (2013). ICT for National Development in Nigeria : Creating an Enabling Environment. International Journal of Engineering and Applied Sciences, 3(2), 59–66.
Prabhakar, S., Pankanti, S., & Jain, A. K. (2003). Biometric Recognition : Security and Privacy Concerns. IEEE Security and Privacy, 1(2), 33–42. https://doi.org/10.1109/MSECP.2003.1193209.
Prasad, N. R. K., & Rajesh, A. (2012). RFID-Based Hospital Real Time Patient Management System. International Journal of Computer Trends and Technology, 3(3), 509–517. https://doi.org/10.1109/ICIS.2007.159.
Priya, J., Alad, A., & Manoj, P. M. E. (2016). Fusion of Palm Print and Iris for Multimodal Biometric Recognition. International Journal of Scientific and Research Publications, 6(5).
Thomas, M. (2004). Is Malaysia's MyKad the 'One Card to Rule Them All’ ? The Urgent Need to Develop a Proper Legal Framework for the Protection of Personal Information in Malaysia ? Melbourne University Law Review, 28(2), 474–551.
 This work is licensed under a: Creative Commons Attribution 4.0 International License
This work is licensed under a: Creative Commons Attribution 4.0 International License
© Granthaalayah 2014-2023. All Rights Reserved.