
ASSESSING PERCEIVED RISK IN MOBILE MONEY ADOPTION UNDER COVID-19: A COMBINED SEM-ARTIFICIAL NEURAL NETWORK TECHNIQUES1 Institute of Finance and Accounting, Faculty of Economics, University of Miskolc, 3515 Miskolc-Egyetemvaros, Hungary. |
|
||
|
|
|||
|
Received 6 December 2021 Accepted 17 December 2021 Published 31 January 2022 Corresponding Author Komlan
Gbongli, pzkgbong@uni-miskolc.hu/ samxp12@yahoo.fr DOI 10.29121/granthaalayah.v10.i1.2022.4434 Funding:
This
research received no specific grant from any funding agency in the public,
commercial, or not-for-profit sectors. Copyright:
© 2022
The Author(s). This is an open access article distributed under the terms of
the Creative Commons Attribution License, which permits unrestricted use, distribution,
and reproduction in any medium, provided the original author and source are
credited.
|
ABSTRACT |
|
|
|
The
introduction of social distancing measures to curb the COVID-19 pandemic and
support the stabilization of the social economy has motivated consumers to do
contactless activities, including mobile money service (MMS). Although this
service remains beneficial to consumers, the adoption rate is still at its
formative stage in Togo. The socio-economic background and peoples'
inclination are hesitant for such rising digital transactions, seemingly due
to risk perception. Therefore, the study develops a model to capture
multidimensional perceived risk regarding the adoption decision. A total of
275 respondents were tested using a hybrid structural equation modeling (SEM)
and artificial neural network (ANN) approach through a multilayer perceptron
(MLP) with feed-forward back-propagation (FFBP) algorithm. The ANN model is
found to seize better performance and high prediction accuracy than SEM
regarding nonlinearity and linearity. Our results suggest that perceived
privacy risk (PRR) stands out as the most critical antecedent of the
perceived overall risk (POR), in which the latter negatively affect the
behavioral intention (BI) to use MMS. This research remains one of the first
to test the acceptance of MMS empirically during the COVID-19 crisis and
contributes both theoretically and practically toward understanding factors
influencing its widespread adoption. To promote citizen's trust, service
providers must provide instructions on using MMS safely and coping with
privacy breaches and security problems if they arise. The SEM-ANN methodology
will aid fulfill the current literature gap of MMS acceptance and provide
practical guidance for evidence-based decision-making. |
|
||
|
Keywords: Artificial
Neural Network (ANN), Mobile Money Service (MMS), Perceived Risk, COVID-19,
Structural Equation Modeling (SEM) 1. INTRODUCTION The world has already
experienced pandemics during its history through the great plague and across
1918 influenza pandemic Taubenberger et al.
(2019). The whole world
has been facing an unprecedented coronavirus health crisis for more than a
year now. However, the COVID-19 pandemic remains one-of-a-kind due to at
least two motives. First, more than three billion told to stay home worldwide
over the virus in March 2020 Beaunoyer et al.
(2020) its magnitude
and impacts are unparalleled. In the middle of 2020, several nations that
initially imposed strict lockdown measures lift them or see doing so.
However, there are considerable differences in policy approaches López and Rodó (2020). The second
deadly epidemic wave during the 1918 influenza pandemic, apparently caused by
strain mutations Martini et al. (2019), has also
motivated a vigorous debate on whether actions should incorporate this option.
Second, there is a |
|
||
significant difference between the period of compulsory isolation we are collectively living in and historical quarantines: the overpowering presence of technology Guitton (2020). Governments and supra-national bodies such as the World Health Organization (WHO) convey their messages and recommendations through online technologies as preferred and privileged channels. More importantly, technology is becoming central to maintain active social interactions. Thus, the Covid19 pandemic crisis intensifies the importance of evidence from information technology (IT), digital transformation such as mobile financial services (MFS).
Considering the evolution of information technology communication (ICT), banking systems adopt technology to patronize bank services efficiently. The mobile money application (MMA) remains a portable technology-based app that has become a considerable payment mode today. It is viewed as a bank subsidiary, with its services used to access and complete financial transactions. According to Gichuki and Mulu-Mutuku (2018), cell phone coverage and usage have exponentially grown. Moreover, the Statista report in 2021 revealed the global LTE (long term evolution) population coverage of around 83 percent, while the newest mobile technology (i.e., 5G) covered approximately 15 percent in 2020. Therefore, MMA services are seen as a potential solution to support financial transactions Tchouassi (2012). The number of cell phone subscriptions in Africa increased speedily from a 22.9% share of the population in 2005 to 89.4% in 2013 Chaix and Torre (2015). However, less than 25% of the adult population had a bank account in the same period Demirgüç-Kunt and Klapper (2013). Thus, an increase in mobile telephony users and Internet penetration seems to have a high potential for opening up access to financial services for unbanked people in developing countries Assadi and Cudi (2011) and massive growth in the adoption and use of the MMA services community. Given the current global crisis, it would also be sensible to indicate that currency notes have been conditioned to be the carrier of microorganisms and deadly viruses Alemu (2014). Recently, currency notes were emphasized to factor in spreading coronavirus (COVID-19) to the point that banknotes circulated in Europe and Asia were quarantined for some days Lucre (2020). Many business operators have also decided not to accept banknotes from customers Lucre (2020). The adoption of e-money becomes much more practical and indeed safer than physical currency; therefore, enough to encourage people to switch to e-money, mainly in emerging market societies. Despite IT advancements, there are still many questions about adopting mobile money services (MMS).
In the context of Togo, mobile money users commonly transfer money to a relative. Equally, users adopt services to pay service bills such as electricity, water, telephone, and TV subscription and pay in supermarkets and restaurants (see African Development Bank report 2015) Assadi and Cudi (2011). As reported by the central bank of West African States (i.e., BCEAO in French) in 2016, the banking rate in Togo was less than 15%. In contrast, approximately 67% of the populace subscribed to mobile telephony in 2014 Couchoro (2016). Furthermore, in the West Africa Economic and Monetary Union (WAEMU) zone, by the end of 2019, mobile money recorded 76.97 million account openings and 2.633 billion transaction volume at about 28.738 billion FCFA value transactions with a variation of 37.9% between 2018/2019. Togo's share was lower than 6% of account openings, volume, and the aggregate value of transactions BCEAO (2020). FCFA is the franc of the African Financial Community (Benin, Burkina Faso, Côte d'Ivoire, Guinea-Bissau, Mali, Niger, Senegal, and Togo), 1 dollar US is approximately 545 FCFA. From the overview of MFS data, Togo is lagging in the adoption of mobile money in the WAEMU zone. As a result, mobile money is expected to make a substantial impact in increasing the rate of access to financial services. On the ground, this is far from being the case.
Mobile money provides numerous benefits, yet, it has been demonstrated to be a double-edged sword. For instance, it may offer many advantages such as faster transaction speed, 24-hour availability, reducing operational cost. Still, it poses a range of risks and threats such as malware, spyware, phishing, spoofing, and password-sniffing De Kerviler et al. (2016), Narteh et al. (2017). In Togo, with mobile money services (MMS) at the developing stage, customers' motive for resisting such services could be attributed to their perceived risk of conducting online transactions Gbongli et al. (2017). Thus, it is crucial to embrace and acknowledge risk for the growth and development of emerging economies Singh and Gaur (2018). Although the concept of perceived risk has been explored in several kinds of literature Lee (2009), Martins et al. (2014), Roy et al. (2017), Abdul-Hamid et al.(2019), Susanto et al. (2020), not many studies have focused on the specific context of predicting and ranking the type of risk directly through the aggregate perceived risk by using a combined methodology. Studies relating to the effect of perceived risk on customer intention to adopt and using e-money services have not been of much concern among researchers, especially in the perspective of a developing economy. Previous studies have considered the perceived risk as one of the inhibitors in digital money adoption, and it has yet to be conceptualized and examined on a multidimensional scale Koenig-Lewis et al. (2015). Therefore, it is necessary to study the resistance factors in using MMS to raise its adoption rate among consumers. Several researchers have also highlighted those different contextual aspects must be integrated to fundamentally assess customers' behavior in technology acceptance and use Hashim et al. (2015), Venkatesh et al. (2012a). This model considers the customer perceived dimensions outlined by Featherman and Pavlou (2003) to shed some light on the components that hinder e-money acceptance.
The importance of this research is twofold. First, this research can address the gap in the extant mobile money literature by offering empirical evidence and theoretical supports regarding MMS inhibitors during the pandemic. Thus, this study herein develops and empirically validates a research framework that can examine the relationship between the multidimensional perceived risk (i.e., privacy, time, security, and monetary risk) and perceived overall risk (POR) into a model. It also presents the relation between POR and consumers' behavioral intention (BI) towards MMS adoption. Second, we examine a two-stage methodology, i.e., structural equation modeling (SEM) - artificial neural network (ANN), to develop and test a model that can better predict consumers' POR to use innovative technology such as MMS. Therefore, the study uses an SEM-ANN approach in capturing linear-nonlinear and non-compensatory relations between the exogenous and endogenous variables. With this methodology, the complexity of consumer decision-making on resistance to mobile money service is better explained.
The significance of the contribution revealed that perceived privacy risk singled out as the most critical influence on the perceived overall risk, in which the latter negatively impact the behavioral intention to use MMS. Therefore, a new connection to the determinant of overall risk and intention to use MMS is uncovered. This result suggests new ideas which are essential for policy formulation. MMS companies' providers should formulate strategies that would most effectively reduce an individual's concerns toward these services. This can be done by integrating advanced data management techniques such as data encryption platforms to guarantee security in financial transactions and promoting citizen's trust since privacy seems superfluous when security is present. Furthermore, the integrated SEM-ANN (capturing linear-nonlinear and non-compensatory relations between variables) improves existing alternatives' accuracy, so a particular open question is resolved. Therefore, the study extends existing methodologies and research practices in such that using ANN is another step forward from the traditional linear regression techniques.
The paper is outlined in various sections. Its starts with an introduction followed by a review of existing studies. Then, we propose the hypothesis and the research model. The following section details the used methodology, while section five presents the data analysis with research results. Lastly, we conclude the study with implications, limitations, and suggestions for future research.
2. LITERATURE REVIEW AND THEORETICAL FRAMEWORK
2.1. PROMOTING MOBILE MONEY USAGE TO CURB THE SPREAD OF THE COVID-19 PANDEMIC
The demand for accessing and understanding online information and following recommendations are crucial as far as the capacity of individuals to take protective actions are required. Since starting the COVID-19 pandemic, digital spaces have been the central channel government and official agencies, including the World Health Organization (WHO), have employed to disseminate information regarding the measures that people must implement to avoid getting contaminated and contaminated others Lee et al. (2008). Under the numbers of COVID-19 cases that upsurge, many people are choosing cashless payments to prevent direct contact and potential hygiene concerns due to banknotes, which may facilitate the spread of the COVID-19. This situation increases the call of digital payments, predominantly mobile money – a service in which the mobile phone is employed to access financial services – to those who have not considered this transaction method.
Mobile money has various features that can support undisrupted financial transactions in the present pandemic. The World Health Organization has enumerated several ways to prevent the spread of the COVID-19 virus. Some of these methods have led people to avoid direct contact with other people while driving communities to use digital payment options as an alternative for day-to-day transactions. Moreover, many countries have imposed "lockdown," which has led various banks, money exchange providers, and retail businesses to reduce their hours of operation or even close altogether. Therefore, mobile money has turned to be an attractive option for making payments. Several governments and retail businesses have also discouraged the use of physical cash for making transactions. Conversely, mobile money enables account holders to transfer e-money and conduct other financial transactions with minimal physical contact, helping alleviate the spread of the virus.
Studies have shown that notes and coins can spread bacteria and germs, facilitating the spread of the COVID-19 virus. However, digital imbalances continue increasing the vulnerability to the COVID-19 virus and crisis concerns Beaunoyer et al. (2020). Decreasing or ideally eliminating physical cash transactions and creating digital money opportunities could help stop the spread of bacteria and germs. According to a World Economic Forum publication, the move away from cash is also vital in emerging markets Reuters Staff (2020). Africans are urged to switch to digital payment alternatives to reduce the coronavirus risks of exchanging money in cash. From this end, Kenya's government has explored ways of expanding mobile money usage to curb the risk of spreading the virus through the physical handling of cash. Similar actions were undertaken to reduce the risk of COVID-19 transmission through mobile money in Ghana, Nigeria, and Uganda. It has been reported that mobile money service (MMS) usage during the pandemic has grown by 6% across the globe, with West Africa experiencing the most significant upsurge of MMS usage Reuters Staff (2020).
There are two distinct phenomena related to digital money that have contributed to fighting during the pandemic. One part is that banknotes and coins were assumed to be carrying the virus, and digital payment was desired to the "dirty money" Sangster (2020), Kelly (2020). Online delivery services were urging customers to make payments using digital payment systems such as credit/debit cards or mobile payments, which were enforced or mandated by the government in several parts of the world, such as India Kapoor (2020). Lastly, during the lockdown, there was a loss of jobs. Various governments, including Togo, offered cash transfer programs to assist vulnerable households via payment apps and digital payment modes. These are a convenient approach of fund transfer from donors to recipients, as seen in earlier crisis relief situations Pollach et al. (2005). Grounded in earlier crisis and disaster events, where the mobility of citizens was restrained, many MMS providers (e.g., Vodafone in Afghanistan and Safaricom in Kenya) have offered a fast fund transfer of remittances from migrants to their homes and relief aid from the government to victims Aker et al. (2016), Wachanga (2015). A similar situation has been observed during the COVID-19 pandemic, requiring scholars for future study De et al. (2020). Despite the disruption in the global economy, it is crucial to note that mobile money has proven to be a valuable tool in enabling safe and efficient financial transactions throughout the pandemic.
2.2. PERCEPTION OF RISK IN MOBILE MONEY SERVICES
The concept of perceived risk in marketing literature
was introduced by Bauer Bauer
(1960). It is considered a
fundamental principle to determine the uncertainties or unfavorable outcomes of
searching and choosing products or services before making any purchasing
decision or both Kesharwani
and Bisht (2012). Various studies have
paid particular attention to concerns related to the perception of risk Curran
and Meuter (2007), Flavián
et al. (2006). In the context of
online business, the possibility of unfavorable results remains somewhat high
due to the intrinsically risky environment of the internet, intangibility, lack
of control, anonymity, security, and privacy protection characterized in the
mobile financial services (MFS) area along with the absence of human
interaction Pavlou (2003), Alalwan
et al. (2017), Featherman
and Pavlou (2003), Martins
et al. (2014).
Perceived risk is claimed to be a multifaceted construct, as studied by numerous researchers. For instance, Lee et al. (2003) stressed that Jacoby and Kaplan's risk dimensions model Jacoby and Kaplan (1972) is inherent and suitable to the mobile financial service study. Featherman and Pavlou (2003) empirically tested such a risk model in the perspective of internet-delivered e-service acceptance by substituting the physical risk dimension with privacy risk, which is a more pronounced risk factor in online service. Zhao et al. (2008) identified four significant risk factors (risk of losing personal control, losing face, system failure, and the risk of exhibiting problems to others) as the main level of perceived risk measurement. Equally, Littler and Melanthiou (2006) acknowledged six main aspects of perceived risk (psychological, security, financial, performance, time, and social) related to the decision of consumer acceptance of internet banking services during the initial stages of market development. Other scholars have also emphasized the essential features of perceived risks that support consumers' decisional intention, such as Hanafizadeh and Khedmatgozar (2012) (time, financial, performance, social, security, and privacy risk).
This work partially adopts the risk dimensions suggested by Featherman and Pavlou (2003) and further advances the study on perceived risk by including transaction security risk. Given the results of the earlier studies coupled with summarizing the notions of the dimensions of the perceived risk, this study considers perceived risk from four angles, namely: privacy, time, security, and financial in the form of monetary.
3. HYPOTHESIS DEVELOPMENT
3.1. MULTIDIMENSIONAL PERCEIVED RISK AND OVERALL PERCEIVED RISK
The perception of risk exposure of a mobile money service (MMS) client is a possible barrier to accepting the service. It is then essential to review the various aspects of the risk dimensional to the overall risk and how it might influence the consumers' intention to use MMS.
Regarding the potential perceived risk facet, privacy denotes the ability of an individual or organization to decide on whether, when, and to whom personal or organizational information should be released Saltzer and Schroeder (1975). Therefore, privacy differs from security, which is the mechanisms and procedures that control who may use or change the device (i.e., computer, cell phone) or the information stored in it Saltzer and Schroeder (1975). Privacy risk involves individual users, their behavior, and relationships with others, while security risks entail risks posed by adversaries attacking or threatening a system Hong et al. (2004), Palen and Dourish (2003) stressed that managing privacy involves handling ever-changing situations rather than implementing existing rules. Services that carefully deal with privacy issues are expected to protect clients from any possible risks, loss, or fraud. Hence, users may have increased trust in the service providers that decrease individual privacy issues and improve overall customer satisfaction Liang et al. (2014).
In connection to the online environment, Liu et al. (2008) have also shown that security and privacy are decisive factors that patronize the prediction of Chinese customers' online shopping satisfaction. Moreover, Sakhaei et al. (2014) highlighted the significance of privacy and security and their impact on service quality in internet banking, which eventually affects customer contentment. Therefore, the perception of risk associated with privacy and security plays a fundamental role in consumer decision-making behavior. As such, security and privacy risks constrain customers to allocate extra time and effort to protect against frauds and hackers, which leads them to observe mobile financial services as a problematic way to do banking activities Daneshgadeh and Yıldırım (2014).
Equally, time risk ascends when customers devote more time handling erroneous transactions, filling in the necessary information, and waiting for site responses, website confirmation, internet server, and download speed Kaur and Arora (2020). Considering the environment of mobile money service, a customer may feel that the service provider will not deliver the expected standard of service, causing loss of money (perceived financial cost or monetary risk) and time lost understanding (perceived time).
Regarding monetary risk, it refers to the consumer's perception of a particular online channel (mobile money services in our study) costing more money than alternative purchase channels Luarn and Lin (2005). The adoption rate of MMS among the unbanked populace is associated with the cost of making transactions using the service Tobbin (2012). From this perspective, individuals are likely to adopt mobile money services if their perception of the related expense is acceptable compared to other existing service options Luarn and Lin (2005). Some studies conducted in emerging economies such as China Yao and Zhong (2011), Brazil Cruz et al. (2010), and Bangkok Sripalawat et al. (2011) have explicitly found monetary risk as a barrier to the adoption of mobile financial services. Once individuals consider the cost of mobile phones high, the purchasing of SIM cards to be high, and the cost of registration and other transaction costs to be higher, their intention to evaluate the perceived overall risk would be necessary.
Based on the above discussion regarding the multidimensional risk facet toward the perceived overall risk, the following hypotheses can be proposed:
H1. Perceived
privacy risk has a positive and significant influence on perceived overall
risk.
H2. Perceived
time risk has a positive and significant influence on perceived overall risk.
H3. Perceived
security risk has a positive and significant influence on perceived overall
risk.
H4. Perceived
monetary risk has a positive and significant influence on overall perceived
risk.
3.2. OVERALL PERCEIVED RISK AND BEHAVIORAL INTENTION
Risk perception denotes the probability of contrary results obtained from the application of online services, including transaction security, hacking and phishing attempts by fraudsters, internet deficiencies, or malfunction of online websites or apps Kesharwani and Bisht (2012). All these fears could prevent customers in the use of MFS. Indeed, aspects related to the perceived risk, in general, have been widely regarded as crucial negative determinants of customers' intentions and the adoption of information systems (IS), thus mobile money services (MFS) Cunningham et al. (2005), De Kerviler et al. (2016), Roy et al. (2017). The explanation of the negative relationship between perceived risk and behavioral intention can be obtained through attitude, which usually prompts action derived from the theory of reasoned action (TAM) Fishbein and Ajzen (1975). Based on the consistency with this leading theory, it is predicted that decreasing perceived risk will enhance customers' willingness to transact. This phenomenon regarding the attitude-action principle has mainly been elucidated by Kesharwani and Bisht (2012) because perceived risk in online transactions decreases behavioral and environmental control perceptions. This absence of control, in turn, mitigates the customers' behavioral intentions. Given the concept of this reasoning, it is expected that customers are likely to transact online if their risk perceptions concerning behavioral and environmental fears are mitigated. Hanafizadeh et al. (2014) indicated that risk aspects are essential in mobile services, and the higher the risk of using new technology, the lower is the willingness to use it. Therefore, it is assumed that if a customer perceives more threats in mobile money services, he/she will not be inclined to use them. However, reducing the perception of risk in mobile money will boost the customers' intention to use it.
Understanding the low penetration rate of MFS and given that its resultant likely lack of considerable risk-based protection measurement, we predict that individuals will develop resistance to this novel technology and form a reasonably negative evaluation of it as a new mode of payment. Therefore, the following hypothesis is proposed:
H5. Perceived
overall risk has a negative and significant influence on behavioral intention
to use mobile money services.
Grounded on these research hypotheses, the research model set to study the customer behavioral intention to use mobile money services is depicted in Figure 1.
|
|
|
Figure 1 Proposed research model NB:
PRR-Perceived privacy risk; TIR-Perceived time risk; SER-Perceived security
risk; MOR-Perceived monetary risk; POR-Perceived overall risk; and
BI-Behavioral intention to use |
4. RESEARCH METHODOLOGY
Based on the study's objectives to examine the multidimensional effect of perceived risk on the overall risk perception towards the Togolese customers' intention of mobile money service, a sampling frame entails mobile money customers residing in a capital city Togo: Lome. For testing the model and hypotheses, survey-based research designs were employed to collect quantitative data from many respondents. A structured questionnaire was developed based on the proposed model and distributed amongst Togolese customers (potential and actual users) of mobile money (e.g., T-money and Flooz). For respondents who were anxious to deal with hard copies of the questionnaire or get contaminated and contaminated others because of possible virus transmission, their responses provided regarding each item have been filled by the investigators. The questionnaires were to target consumers acquainted with the various service offerings by financial institutions and understand them well enough to respond.
Furthermore, the questionnaire was not lengthy and did not require too much time to fill it. The data collection lasted for one month. A purposive sampling technique was applied to choose the various study areas, and simple random sampling was most used to sample the subscribers. The simple random method was used to give an equal chance to the users of the service. Among the question items presented in the existing literature, those applicable to mobile financial services were separately extracted and partially used. Notably, the tools that measure perceived risk privacy were adapted from Cheung and Lee (2001) and Flavián and Guinalíu (2006) perceived time was measured by adjusting the instrument from Nam and Quan (2019) and Yang et al. (2015). The scales of perceived security risk were derived from Featherman and Pavlou (2003) and Yang et al. (2015) perception of monetary risk was adapted from Kuisma et al. (2007) and Fain and Roberts (1997). The items of perceived overall risk were adapted from Featherman and Pavlou (2003) and Roy et al. (2017), constructs regarding the customer's intention to use mobile money services were adapted from Fred D. Davis MIS. (1989) and Davis et al. (1989). For clarity, a 5-point Likert scale was employed to measure the level of agreement for every item starting from strongly disagree (1) to strongly agree (5). According to Field (2006), such scales are essential to reduce biases in a survey. The complete list of items is given in Appendix. The survey instrument was validated using back-to-back translation, from English to French and then French to English. Two experts, including one professional translator, validated the final version. A total of 320 questionnaires were disseminated. We only received 275 completed and usable responses; thus, our response rate is accounted for 85.94%. Those omitted were due to errors such as partial response or missing data.
5. DATA ANALYSIS
5.1. PROFILE OF RESPONDENTS
Table 1 shows the 275 respondents' demographic profile, of which 53.9% of them were female and 46.1% were male. Most of the respondents were reasonably young which 28% were below 25years, and 34.9% were between 25 and 34 years, 19.6% were between 35 and 44, while 17.5% were 45 years old and above. Regarding their academic qualifications, most respondents were secondary school levers at 40%, followed by university degree holders at 26.2%, and high school (A level) at 23.3%. In contrast, people with no formal education were only 10.5%.
|
Table 1 Demographic profile of respondents |
|||
|
Variables |
Classification |
Total (N=275) |
|
|
N |
% |
||
|
Gender |
Female |
148 |
53.9 |
|
Male |
127 |
46.1 |
|
|
Age |
18-24 |
77 |
28 |
|
25-34 |
96 |
34.9 |
|
|
35-44 |
54 |
19.6 |
|
|
45
or more |
48 |
17.5 |
|
|
Education
level |
No
formal education |
29 |
10.5 |
|
Secondary
school |
110 |
40 |
|
|
Higher
school |
64 |
23.3 |
|
|
University |
72 |
26.2 |
|
5.2. STRUCTURAL EQUATION MODELING
The proposed model is evaluated through a two-phase approach, recommended by Anderson and Gerbing (1988) for structural equation modeling (SEM). The first part requires assessing the measurement model to investigate the reliability and validity of the relationships between the latent variables and the related observable variables. The second part focuses on testing the structural relationship among the theoretical constructs Hair et al. (2006). The artificial neural technique is adopted for predicting and classifying the various antecedents of perceived overall risk toward the intention of using mobile money services. Data analysis was conducted using the statistical package for social sciences (SPSS 21) and analysis of moment structures (AMOS 20) to estimate the model parameters.
5.2.1. MEASUREMENT MODEL ASSESSMENT
Confirmatory factor analysis (CFA) was performed to
evaluate the factor structure and validate the scales Hair et
al. (2010) using AMOS 21
software. The suggested model was tested for model fit, reliability, convergent
validity, and discriminant validity at the earliest stage. The model was found
to be sufficiently fit with Chi-Square![]() Chisq/df (
Chisq/df (![]() ,
goodness of fit index
,
goodness of fit index![]() ,
adjusted goodness of fit index
,
adjusted goodness of fit index![]() ,
normed fit index
,
normed fit index![]() ,
Tucker-Lewis index
,
Tucker-Lewis index![]() ,
comparative fit index
,
comparative fit index ![]() and root mean square error of approximation
and root mean square error of approximation![]() .
.
Second, the constructs' reliability was evaluated using two indicators – Cronbach's alpha (CA) and composite reliability (CR) (Bagozzi and Yi (1988). As shown in Table 2, CA and CR for each construct were above the recommended threshold limit of 0.7, indicating a high level of internal consistency Bagozzi and Yi (1988), Bagozzi and Yi (1988), Bagozzi and Yi (1988), Bernstein and Nunnally (1994). Convergent validity items were assessed grounded on average variance extracted (AVE). The AVE determines the amount of variance captured by a construct relative to measurement error. It should be above 0.5 so that more than half of the variance of its indicators can be enlightened by the latent construct Hair et al. (2010). Table 2 shows that AVE for each construct ranged from 0.571 to 0.664, which were well above the minimum required level of 0.5. Therefore, this study showed convergent validity for all constructs.
Finally, discriminant validity was assessed using criteria based on the correlation matrix or cross-loadings Fornell and Larcker (1981). It states that the square root of AVEs for each construct should be greater than the correlations among the respective constructs Fornell and Larcker (1981). As shown in Table 2, all the diagonal AVE elements were greater than those in the corresponding rows, satisfying Fornell-Lacker's criteria of discriminant validity Fornell and Larcker (1981). In sum, the above figures demonstrated the soundness of the measurement model of this research.
|
Table 2 RELIABILITY AND VALIDITY IN CFA |
||||||||||||
|
Construct |
CR |
AVE |
MSV |
PRR |
TIR |
SER |
MOR |
POR |
BI |
|||
|
PRR |
0.862 |
0.609 |
0.057 |
0.78 |
||||||||
|
TIR |
0.855 |
0.664 |
0.227 |
0.144 |
0.815 |
|||||||
|
SER |
0.843 |
0.577 |
0.056 |
0.011 |
0.235 |
0.76 |
||||||
|
MOR |
0.856 |
0.6 |
0.133 |
0.238 |
-0.022 |
-0.072 |
0.775 |
|||||
|
POR |
0.811 |
0.594 |
0.065 |
0.232 |
0.091 |
0.035 |
0.255 |
0.771 |
||||
|
BI |
0.799 |
0.571 |
0.013 |
-0.004 |
-0.035 |
0.086 |
0.075 |
0.115 |
0.757 |
|||
|
Note: Diagonal values are squared roots
of AVE; off-diagonal values are the estimates of inter-correlation between
the latent constructs. NB: PRR-Perceived privacy risk; TIR-Perceived time
risk; SER-Perceived security risk; MOR Perceived monetary risk; POR-Perceived
overall risk; and BI-Behavioral intention to use |
||||||||||||
5.2.2. STRUCTURAL MODEL ASSESSMENT
The next step in the analysis was to examine the
structural model and associated hypothesized theoretical relationships. The fit
statistics of the structural model (![]()
![]()
![]() ,
,
![]() ,
,
![]() ,
,
![]() ,
,
![]() ,
,
![]() )
were above the suggested threshold limit, indicating an adequate model fit. The
properties of the causal paths, inclusive of standardized path estimates and
t-statistics (CR obtained from AMOS) for the model, are conveyed in Table 3. The result revealed
that the behavioral intention is negatively explained by perceived overall risk
(
)
were above the suggested threshold limit, indicating an adequate model fit. The
properties of the causal paths, inclusive of standardized path estimates and
t-statistics (CR obtained from AMOS) for the model, are conveyed in Table 3. The result revealed
that the behavioral intention is negatively explained by perceived overall risk
(![]() ).
Perceived overall risk, which is hypothesized to be significantly influenced by
perceived privacy risk
).
Perceived overall risk, which is hypothesized to be significantly influenced by
perceived privacy risk ![]() ,
perceived security risk
,
perceived security risk ![]() and perceived monetary risk (b = 0.148, p <
0.001), was supported. Yet, the path coefficient of perceived time risk
and perceived monetary risk (b = 0.148, p <
0.001), was supported. Yet, the path coefficient of perceived time risk ![]() on the overall perceived risk was recognized
as non-significant. The threshold level of t-values is 1.68 at 0.10, 1.96 at
0.05, 2.57 at 0.01, and 3.3 at 0.001 levels. Therefore, except for H2
(TIR→POR), all research hypotheses (H1, H3, H3, and H4) were supported
(see Table 3).
on the overall perceived risk was recognized
as non-significant. The threshold level of t-values is 1.68 at 0.10, 1.96 at
0.05, 2.57 at 0.01, and 3.3 at 0.001 levels. Therefore, except for H2
(TIR→POR), all research hypotheses (H1, H3, H3, and H4) were supported
(see Table 3).
Furthermore, statistical results regarding the
collinearity test assured no concern regarding multi-collinearity since all
values of variance inflation factors (VIF) and tolerance were observed to be
within the acceptable value of 5 and 0.2, respectively Hair et al. (2017). Checking ![]() values, multidimensional perceived risk
predicts 35% of variance for perceived overall risk, where the latter indicates
20.6% of intention variables. It can be said that these values meet the
reasonable criteria over 0.19 to confirm the model validity Hair et al. (2012).
values, multidimensional perceived risk
predicts 35% of variance for perceived overall risk, where the latter indicates
20.6% of intention variables. It can be said that these values meet the
reasonable criteria over 0.19 to confirm the model validity Hair et al. (2012).
|
Table 3 Results of standardized estimates of the structural model |
|||||||
|
Hypothesis |
Causal path |
Path
Coefficients |
t-value |
P-value |
Significance? |
||
|
H1 |
PRR |
à |
POR |
0.309 |
8.987 |
*** |
YES |
|
H2 |
TIR |
à |
POR |
0.032 |
0.951 |
0.346 |
NO |
|
H3 |
SER |
à |
POR |
0.143 |
4.806 |
*** |
YES |
|
H4 |
MOR |
à |
POR |
0.148 |
4.477 |
*** |
YES |
|
H5 |
POR |
à |
BI |
-0.205 |
-3.416 |
0.003 |
YES |
|
* p<0.05; ** p<0.01; ***
p<0.001 level of significant NB: PRR-Perceived privacy risk; TIR-Perceived
time risk; SER-Perceived security risk; MOR-Perceived monetary risk;
POR-Perceived overall risk. and BI-Behavioral intention to use |
|||||||
5.3. NEURAL NETWORK ANALYSIS (ANN)
This research adopts a multi-analytical technique by integrating SEM and ANN, one of the most important artificial intelligence methods. Haykin (1999) describes ANN as a massively parallel distributed processor consisting of mere processing units, which have a neural tendency to store experimental knowledge and make it accessible for application. The acquired knowledge from learning processes is stored in synaptic weights Liébana-Cabanillas et al. (2018). The neural network model in this study was developed using the popular statistical package IBM SPSS 21.0, which played an essential part in modern artificial intelligence techniques and was trained by a multilayer perception training algorithm.
Various researchers have considered the most commonly adopted neural network model –feed-forward back-propagation multilayer perceptron (FFBP-MLP) Wong et al. (2021), Dumor and Gbongli (2021)in the field of business to assess and predict dependent variables based on independent variables Sharma (2017) Liébana-Cabanillas et al. (2018), Gbongli et al. (2019). The multilayer perceptron network is a function of predictors (i.e., inputs or independent variables) that reduce the prediction error of target variables (i.e., outputs). The MLP entails three layers, i.e., input, hidden, and output layers. Therefore, to train and test the research model in this study, we have applied a multilayer perceptron (MLP) with feedforward-back propagation (FFBP) algorithm. The input signals are fed in a forward direction, while the error signals propagate backward.
Determining the number of neurons in the hidden layers
is crucial in deciding the overall neural network architecture. The analysis
examined the network with one to ten hidden nodes. There is no heuristic method
to identify the number of hidden nodes in an ANN, so the trial-and-error and
rules-of-thumb are usually used Chan and Chong (2012), Chong (2013). One of the most
commonly known empirically driven rules-of-thumb concerns the ideal number of
hidden neurons as mostly between the number of input and number of the output
neurons Blum (1992). Another rule is equal
to ![]() size of the input layer and output layer Xu and Chen (2008). Various scholars
recommended other practices that regard the ideal number of hidden neurons
based on both input and output neurons Sheela
and Deepa (2013). For instance, Shibata
and Ikeda (2009) proposed that the
number of hidden neurons
size of the input layer and output layer Xu and Chen (2008). Various scholars
recommended other practices that regard the ideal number of hidden neurons
based on both input and output neurons Sheela
and Deepa (2013). For instance, Shibata
and Ikeda (2009) proposed that the
number of hidden neurons ![]() could be computed as follows:
could be computed as follows:
|
|
|
(1) |
Where ![]() – is the number of input neurons and
– is the number of input neurons and ![]() –
is the number of output neurons.
–
is the number of output neurons.
Alternatively, the required numbers of hidden neurons (![]() )
estimated in the hidden layer using multilayer perceptron (MLP) were found by Trenn
(2008) and computed as
follow:
)
estimated in the hidden layer using multilayer perceptron (MLP) were found by Trenn
(2008) and computed as
follow:
|
|
|
(2) |
The crucial points are simplicity, scalability, and adaptivity. Some scholars, including Yao et al. (1999), have also suggested logarithmic dependence, even more, straightforward and practical guidelines, between the number of hidden neurons and the number of inputs:
|
|
|
(3) |
In the same vein, Fang and Ma (2009) quite similarly stating:
|
|
|
(4) |
Notwithstanding its importance, there is no unique rule for choosing the optimum number of hidden neurons. In the presence of unstable models, the number of hidden neurons becomes too large or too small. A tradeoff is made that when the hidden neurons reach a considerable number, the output of neurons becomes unstable. When the number of hidden neurons becomes too small, the output neurons become unstable again. It is essential to mention that, to some extent, all these rules of thumb should be tested before the final application.
In most cases, the network that performs best on the testing set with the least number of hidden neurons should be chosen. Furthermore, many other elements can affect the choice of the number of hidden neurons, such as the number of hidden layers, the sample size, the neural network architecture, the complexity of the activation function, the training algorithm, etc. Sheela and Deepa (2013). Since there is no dominant rule, and in various situations, the suggestion provided by simulation software is adopted Liébana-Cabanillas et al. (2018).
In this study, the number of neurons in a hidden layer was varied to observe the impact of the hidden layers on the neural network's performance. The results revealed that three neurons in the hidden layer were optimal, and therefore they were chosen to train the networks. The network structure settled for data involved an input layer, one hidden layer, and an output layer. The input layer consisted of four neurons, three neurons in a hidden layer, and one neuron in the output layer (see Figure 2). The input layer entails four independent variables: the output obtained Covariance-based structural equation modelling (CB-SEM) (i.e., perceived privacy risk, perceived time risk, perceived security risk, and perceived monetary risk). The output layer was made of one output variable (i.e., perceived overall risk). The nodes' number in one hidden layer was set to 2 based on recommendations provided above, and the activation function was set to sigmoid function in both hidden and output layers Leong et al. (2013), Gbongli et al. (2019). Given the improvement of the training effectiveness or shorter training times and better performance, both inputs and outputs were normalized to the range [0,1] Negnevitsky (2011).
|
|
|
Figure 2 The schematic model of ANN MLP
4-3-1 |
The accuracy can be measured based on the root-mean-square of error (RMSE), suggested by Hyndman & Koehler Hyndman and Koehler (2006). Therefore, for assessing the model's predictive accuracy, the RMSE of both training and testing data sets is calculated for all ten neural networks, with the computation of the averages and standard deviations (see Table 4). RMSE is always positive, and the value of 0—revealing a perfect fit—has virtually never occurred in practice. Put differently, lower values of RMSE are desired, and the assessment of RMSE can be computed below:
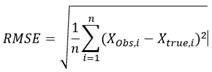 (5)
(5)
Where ![]() is the observed value,
is the observed value, ![]() represents the actual value considered equally
to the model value, and
represents the actual value considered equally
to the model value, and ![]() represents
the number of data sets, i.e., 275 for this study.
represents
the number of data sets, i.e., 275 for this study.
|
Table 4 Neural network validation results |
||
|
ANN |
Input
neuron: PRR, TIR, SER, and MOR; output neuron: POR |
|
|
Training |
Testing |
|
|
ANN1 |
0.1147 |
0.0415 |
|
ANN2 |
0.1146 |
0.0398 |
|
ANN3 |
0.1144 |
0.0411 |
|
ANN4 |
0.1174 |
0.0317 |
|
ANN5 |
0.1182 |
0.0339 |
|
ANN6 |
0.1127 |
0.0449 |
|
ANN7 |
0.115 |
0.0409 |
|
ANN8 |
0.1167 |
0.0342 |
|
ANN9 |
0.1122 |
0.0457 |
|
ANN10 |
0.1177 |
0.031 |
|
Mean RMSE |
0.1154 |
0.0385 |
|
Standard deviation |
0.0073 |
0.0481 |
As revealed earlier, to avoid over-fitting, ten-fold cross-validation was applied, where 90% of the data were considered to train the ANN, whereas the remaining 10% data points were selected to measure the trained network's prediction accuracy. The RMSE values obtained from the neural network model for training and testing data points are minimal (i.e., 0.1154 for training data and 0.0385 for testing data). Therefore, the results obtained are pretty accurate Liébana-Cabanillas et al. (2018).
Sensitivity analysis: The importance of every independent variable computed as a sensitivity analysis is a measure of how much the value predicted by the network model diverges with different values of the independent variable Chong (2013). The relative importance of variables determines the normalized importance, which can be expressed as the ratio of relative importance to its highest relative importance and is also generally disclosed in percentage Sharma et al. (2019). Table 5 summarizes the average relative importance and normalized relative importance obtained from the neural network model.
|
Table 5 Importance of constructs |
||||
|
Network |
Output
neuron: perceived overall risk (POR) |
|||
|
PRR |
TIR |
SER |
MOR |
|
|
ANN1 |
0.732 |
0.121 |
0.055 |
0.091 |
|
ANN2 |
0.678 |
0.141 |
0.018 |
0.163 |
|
ANN3 |
0.737 |
0.141 |
0.034 |
0.089 |
|
ANN4 |
0.652 |
0.178 |
0.029 |
0.142 |
|
ANN5 |
0.511 |
0.081 |
0.168 |
0.24 |
|
ANN6 |
0.696 |
0.164 |
0.025 |
0.116 |
|
ANN7 |
0.79 |
0.119 |
0.041 |
0.05 |
|
ANN8 |
0.753 |
0.119 |
0.031 |
0.097 |
|
ANN9 |
0.754 |
0.132 |
0.045 |
0.068 |
|
ANN10 |
0.573 |
0.184 |
0.072 |
0.171 |
|
Average relative importance |
6.876 |
1.38 |
0.518 |
1.227 |
|
Normalized importance (%) |
100 |
20.1 |
7.5 |
17.8 |
|
NB: PRR-Perceived privacy risk;
TIR-Perceived time risk; SER-Perceived security risk; MOR-Perceived monetary
risk; POR-Perceived overall risk; and BI-Behavioral intention to use |
||||
According to the sensitivity analysis performance, perceived privacy risk was the most significant predictor of the overall perceived risk, followed by perceived time risk, perceived monetary risk (financial risk), and perceived security risk. Interestingly, perceived time risk contradicts the results obtained from SEM. It was found not supported in the SEM results. However, it is the second most influential element in the neural network model, predicting perceived overall risk toward using mobile payment services. The disparity between results achieved by the structural equation model and neural network model can be clarified by the nonlinear and non-compensatory nature of the neural network model and the much higher-order prediction capability of the later model.
6. CONCLUSION AND IMPLICATION
The increasing prevalence of smartphone use for mobile financial experiences is not yet matched at the rate of mobile phone adoption for money transfer. The low level of mobile money service situations suggests the importance of considering the perceived risk that might impede consumers from conducting e-money transactions through smartphones. Moreover, the COVID-19 pandemic required people to use digital payment applications. However, not all people are comfortable and even willing to use e-money. Though, they are forced to some extent due to the outbreak of the COVID-19 virus. As such, many unpredicted hazards in the environment of modern society can only be limited but not removed entirely, and rational consumers are concerned regarding both benefits and uncertainties in the decision-making process Mitchell (1999). Therefore, consumers could be impacted by risks that they perceive Chan and Lu (2004).
By examining data collected from mobile phone users and mobile money users (current and potential), this research tested and established perceived risk as a multidimensional factor that entailed various risk facets. In providing more detail, the values of reliability indices, validity indices, and all other fit indices were within the established thresholds Hair et al. (2010). Apart from SEM results, this study employed a neural network technique to rank the determinants of overall perceived risk while offering evidence to validate SEM results.
In this study, four dimensions of perceived risk (i.e., privacy risk, time risk, security risk, and monetary risk) were used as potential antecedents of perceived overall risk. It is interesting to point out that only perceived time risk has no statistically significant impact on perceived overall risk. These findings imply that privacy risk, security risk, and monetary risk in mobile money play an essential role in adopting mobile-based services by Lome -Togo residents. Generally, the SEM results, except for time risk, are similar to the earlier studies on conceptualized facet-based perceived risk Featherman and Pavlou (2003), Agarwal and Prasa (1998). Each dimension of perceived risk has a positive influence on the overall perceived risk on mobile money service. Moreover, the moderate to weak positive relationships between the perceived overall risk and their antecedent provide further reinforcement that risk can be researched as a multidimensional phenomenon Zikmund and Scott (1974).
Importantly, SEM results revealed that privacy risk had a strong and significant influence on the overall risk construct (H1: beta = 0.309, p-value < 0.001), making it the most relevant perceived risk facet consumers' decision making when evaluating mobile money services. Conversely, consumers are less concerned in security risks (H3: beta = 0.143, p-value < 0.001). Logically, it might seem that privacy is superfluous when security is present, and security is redundant when privacy is present Kim et al. (2008). The ranking obtained from ANN analysis also supports the influence of privacy risk regarding the overall risk to be the most influential risk factor. This implies that consumers' concerns about privacy contribute greatly to risk perception with money transfer using mobile devices. This result corroborates with the earlier works Turel et al. (2007). Although mobile money incorporates various advantages, perceived risks are associated with this service, particularly potential fraud. The most recurrent forms of fraud allied with mobile money entail identity theft, fake currency deposits, scams such as promotional scams, and phishing, intensified by the abundant use of SIM cards. Acceptance regulations can avoid these illegal activities to reduce and manage risks while still progressing regarding the business goals. A collaborative approach between promoters of mobile financial services, mobile network operators, and regulators should tighten the existing digital consumer protection laws. An efficient mechanism for recourse, compensation, and remedy should be set up to benefit the victims of frauds and cybercrime on the mobile money platform. Therefore, when consumers perceive the effectiveness of privacy policy, the privacy concerns will reduce Sharma et al. (2021).
This study also confirms the positive impact of the monetary risk (i.e., perceived financial risk) on consumers' perceived overall risk in general. That the lower is the cost, and trivial remains the perception of risk. From this view, the involvement aspect of the risk is well pronounced when the price or cost is high, which might prompt consumers to think about the risk of losing money Choffee and McLeod (1973). While privacy risk showed a significant and strong influence on the overall risk, monetary risk (financial risk) did not reveal such an effect. Perceived monetary risk (H4: beta = 0.148, p-value < 0.001) has been considered moderately by consumers in the perception of overall risk toward the adoption of mobile money, although these dimensions are primarily of concern in studies on consumer adoption of electronic financial services Luarn and Lin (2005), Smith, (2006). Potential enlightenment to this could be found in consumer behavior studies which revealed that perceived financial risk is very substantial in some cases that it plays a role separate from the other risk facets Stone and Grønhaug (1993). Another justification could also be that the possibility of spending additional money for a mobile service was not such a big concern for people already accustomed to cell phone use.
By comparing the SEM results and the ANN analyses, the main difference lies in the strength of one variable, which is perceived time risk. The ANN analysis increases the relative importance of the risk perception of time towards the overall risk, whereas; time risk is not statistically significant in SEM. This finding could imply that the perception of risk regarding the time might not have a linear statistical significance and direct influence on the aggregate risk. Concerning the non-validation of perceived time risk, it can be suggested that because mobile money services are a relatively new technology in respondents' view, they lack experience. They might not focus much on time spent using the designated service. Therefore, when the technology is deemed as challenging to learn and/or time-consuming to prepare and use or is in some other way perceived as threatening, it possibly will not be used Carr Jr (1999). It may also be that consumers do not recognize a perception of time as an assurance of risk perceived. This suggests that the impact of time risk perceived is worthy of further development in future studies. MFS companies are encouraged to continue easing the transaction process of MFS in terms of time spent.
Perceived overall risk has a significant negative influence on adoption usage intention. This finding is consistent with earlier findings where perceived risk has been found to be a key factor leading to customer resistance in the usage of mobile and online technologies in Malaysia, Kuwait, Brazil, India, Germany, and Singapore Al-Jabri and Sohail (2012), Amin (2008), Cruz et al. (2010), Thakur and Srivastava (2014), Koenig-Lewis et al. (2010), Riquelme and Rios (2010). Mobile money services payments involve significant uncertainty and risk, and service providers may consider applying advanced encryption technologies such as secured socket layer and third-party certification to build trust in mobile payments Li et al. (2012).
Therefore, this research, which contributes to the perceived risk theory using perceived risk as a multi-dimensional framework within the scope of modern mobile financial service research, is appropriate. The study determines that perceived risk, particularly privacy concerns, prevailed irrespective of the forceful adoption of mobile money due to the COVID-19 pandemic. The use of the two-stage predictive-analytic Scott and Walczak (2009), Gbongli et al. (2020), Gbongli (2017), such as SEM–neural network analysis, offers a more holistic understanding of inhibitors determinant of mobile money acceptance specifically and IT adoption generally and therefore provide substantial methodological support from the statistical point of view. This is because the non-compensatory neural network analysis can complement the weaknesses of compensatory and linear SEM analysis. The study has offered a novel perspective in assessing the key factors of mobile money service acceptance, enriching and closing up the knowledge gaps in the current body of knowledge.
This study offers some practical insights into the decision-makers of telecommunication service providers, mobile financial app developers, and mobile money service (MMS) providers to improve and maintain their customer base. As the findings infer, service providers should focus their resources on mitigating the risk features, supporting and motivating potential consumers. MMS companies should advertise that mobile money transfer is not a risky service by offering positive reviews at the point of sales or mass media. Additional effective risk-preventing policies could include money-back guarantees so that consumers feel more comfortable and safer with the system. In sum, mobile money is an evolving trend and holds great potential for development in Togo. Since the COVID-19 pandemic, it is time for the country to get the service adopted.
7. LIMITATIONS AND FUTURE RESEARCH
This study has some limitations that would pave the way for future research. Notably, the relationships among the constructs were tested using customers from a sole country. Therefore, it will be instructive to conduct similar investigations across different contexts to strengthen the nuances of such constructs in the mobile financial service technology adoption literature. The research model in this study excludes the moderating effect of any variable. It is recommended to study the moderating effect of demographic variables as a future study to understand better the barriers to adopting mobile money from a different population segment. For future work, researchers should consider adding extra constructs such as effort expectancy and trust to increase the model's robustness to yield a better prediction of customers' intention in mobile money adoption. Finally, it would be timely to assess the preference of mobile money due to the stigma and risk of using banknotes, particularly in high-risk situations (i.e., food courts and hospitals), while mitigating the spread of COVID-19 and other microbes.
REFERENCES
Abdul-Hamid, I. K., Shaikh, A. A., Boateng, H. & Hinson, R. E. (2019). Customers' Perceived Risk and Trust in Using Mobile Money Services-an Empirical Study of Ghana. International Journal of E-Business Research, 15(1), 1-19. Retrieved from https://doi.org/10.4018/IJEBR.2019010101
Agarwal, R. & Prasa, J. (1998). A Conceptual and Operational Definition of Personal Innovativeness in the Domain of Information Technology. Information Systems Research, 9(June), 204-215. https://doi.org/10.1287/isre.9.2.204 Retrieved from https://doi.org/10.1287/isre.9.2.204
Aker, J. C., Boumnijel, R., McClelland, A. & Tierney, N. (2016). Payment Mechanisms and Antipoverty Programs : Evidence from a Mobile Money Cash Transfer Experiment in Niger. Economic Development and Cultural Change, 65(1), 1- Retrieved from https://doi.org/10.1086/687578
Al-Jabri, I. M. & Sohail, M. S. (2012). Mobile banking adoption : application of diffusion of innovation theory. Journal of Electronic Commerce Research, 13(4), 379-391. Retrieved from https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2523623
Alalwan, A. A., Dwivedi, Y. K. & Rana, N. P. (2017). Factors influencing adoption of mobile banking by Jordanian bank customers: Extending UTAUT2 with trust. International Journal of Information Management, 37(3), 99-110. Retrieved from https://doi.org/10.1016/j.ijinfomgt.2017.01.002
Alemu, A. (2014). Microbial Contamination of Currency Notes and Coins in Circulation : A Potential Public Health Hazard. Biomedicine and Biotechnology, 2(3), 46-53.
Amin, H. (2008). Factors affecting the intentions of customers in Malaysia to use mobile phone credit cards. Management Research News, 31(7), 493-503. Retrieved from https://doi.org/10.1108/01409170810876062
Anderson, J. C. & Gerbing, D. W. (1988). Structural Equation Modeling in Practice : A Review and Recommended Two-Step Approach. Psychological Bulletin, 103(3), 411-423. Retrieved from https://doi.org/10.1037/0033-2909.103.3.411
Assadi, D. & Cudi, A. (2011). Le potentiel d'inclusion financière du "Mobile Banking". Une étude exploratoire. Management & Avenir, 46(6), 227. Retrieved from https://doi.org/10.3917/mav.046.0227
BCEAO. (2020). Rapport annuel sur les services financiers numériques dans l'UEMOA - 2019. Retrieved from https://www.bceao.int/index.php/fr/publications/rapport-annuel-sur-les-services-financiers-numeriques-dans-luemoa-2019
Bagozzi, R. P. & Yi, Y. (1988). On the evaluation of structural equation models. In Journal of the Academy of Marketing Science (Vol. 16, Issue 1, pp. 74-94). Retrieved from https://doi.org/10.1007/BF02723327
Bauer, R. A. (1960). Consumer behavior as risk taking. In Risk Taking and Information Handling in Consumer Behavior (pp. 389-398). Harvard University Press.
Beaunoyer, E., Dupéré, S. & Guitton, M. J. (2020). COVID-19 and digital inequalities: Reciprocal impacts and mitigation strategies. Computers in Human Behavior, 111, 106424. Retrieved from https://doi.org/10.1016/j.chb.2020.106424
Bernstein, I. & Nunnally, J. (1994). Psychometric Theory, 3rd edn, 1994. McGraw-Hill, New York, 3, 701.
Blum, A. (1992). Neural networks in C++ : an object-oriented framework for building connectionist systems. John Wiley & Sons, Inc.605 Third Ave.
Carr Jr., V. H. (1999). Technology Adoption and Diffusion. Retrieved from https://doi.org/A
Chaix, L. & Torre, D. (2015). Le double rôle du paiement mobile dans les pays en développement. Revue Économique, 66(4), 703. Retrieved from https://doi.org/10.3917/reco.664.0703
Chan, F. T. S. & Chong, A. Y. L. (2012). A SEM-neural network approach for understanding determinants of interorganizational system standard adoption and performances. Decision Support Systems, 54(1), 621-630. Retrieved from https://doi.org/10.1016/j.dss.2012.08.009
Chan, S. & Lu, M. (2004). Understanding Internet Banking Adoption and Use Behavior. Journal of Global Information Management, 12(3), 21-43. Retrieved from https://doi.org/10.4018/jgim.2004070102
Cheung, C. M. & Lee, M. K. (2001). Trust in Internet Shopping : Instrument Development and Validation through Classical and Modern Approaches. Journal of Global Information Management, 9(3), 23-35. Retrieved from https://doi.org/10.4018/jgim.2001070103
Choffee, S. H. & McLeod, J. M. (1973). Consumer decisions and information use, in Ward, S. and Robertson, T.S. (Eds), consumer behavior: theoretical sources. Prentice‐Hall Inc., Englewood Cliffs, NJ.
Chong, A. Y. L. (2013). A two-staged SEM-neural network approach for understanding and predicting the determinants of m-commerce adoption. Expert Systems with Applications, 40(4), 1240-1247. Retrieved from https://doi.org/10.1016/j.eswa.2012.08.067
Chong, A. Y.-L. (2013). Predicting m-commerce adoption determinants : A neural network approach. Expert Systems with Applications, 40(2), 523-530. Retrieved from https://doi.org/10.1016/j.eswa.2012.07.068
Couchoro, M. K. (2016). Challenges faced by MFIs in adopting Management information system during their growth phase : the case of Togo. Enterprise Development and Microfinance, 17(2), 115-131. Retrieved from https://doi.org/10.3362/1755-1986.2016.011
Cruz, P., Neto, L. B. F., Muñoz-Gallego, P. & Laukkanen, T. (2010). Mobile banking rollout in emerging markets : evidence from Brazil. The International Journal of Bank Marketing, 28(5), 342-371. Retrieved from https://doi.org/http://dx.doi.org/10.1108/02652321011064881
Cunningham, L. F., Gerlach, J. & Harper, M. D. (2005). Perceived risk and e-banking services : An analysis from the perspective of the consumer. Journal of Financial Services Marketing, 10(2), 165-178. Retrieved from https://doi.org/10.1057/palgrave.fsm.4770183
Curran, J. M. & Meuter, M. L. (2007). Encouraging Existing Customers to Switch to Self-Service Technologies : Put à Little Fun in their Lives. Journal of Marketing Theory and Practice, 15(4), 283-298. Retrieved from https://doi.org/10.2753/MTP1069-6679150401
Daneshgadeh, S. & Yıldırım, S. Ö. (2014). Empirical Investigation of Internet Banking Usage : The Case of Turkey. Procedia Technology, 16, 322-331. Retrieved from https://doi.org/10.1016/j.protcy.2014.10.098
Davis, F. D., Bagozzi, R. P. & Warshaw, P. R. (1989). User acceptance of computer technology : à comparison of two theoretical models. Management Science, 35(8), 982-1003. Retrieved from https://doi.org/10.1287/mnsc.35.8.982
Demirgüç-Kunt, A. & Klapper, L. (2013). Measuring Financial Inclusion : Explaining Variation in Use of Financial Services across and within Countries. Brookings Papers on Economic Activity, 2013(1), 279-340. Retrieved from https://doi.org/10.1353/eca.2013.0002
De', R., Pandey, N. & Pal, A. (2020). Impact of digital surge during Covid-19 pandemic : A viewpoint on research and practice. International Journal of Information Management, 55, 102171. Retrieved from https://doi.org/10.1016/j.ijinfomgt.2020.102171
Dumor, K. & Gbongli, K. (2021). Trade impacts of the New Silk Road in Africa: Insight from Neural Networks Analysis. Theory, Methodology, Practice, 2021(02), 13-26. Retrieved from https://doi.org/10.18096/TMP.2021.03.02
Fain, D. & Roberts, M. Lou. (1997). Technology vs. Consumer behavior: The battle for the financial services customer. Journal of Direct Marketing, 11(1), 44-54. : AID-DIR5>3.0.CO ;2-Z Retrieved from https://www.sciencedirect.com/science/article/abs/pii/S109499689770731X
Fang, B. & Ma, S. (2009). Application of BP Neural Network in Stock Market Prediction. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) (pp. 1082-1088). Retrieved from https://doi.org/10.1007/978-3-642-01513-7_119
Featherman, M. S. & Pavlou, P. A. (2003). Predicting e-services adoption : à perceived risk facets perspective. International Journal of Human Computer Studies, 59(4), 451-474. Retrieved from https://doi.org/10.1016/S1071-5819(03)00111-3
Field, A. (2006). Discovering statistics using SPSS (2nd Editio). SAGE Publications, London.
Fishbein, M. & Ajzen, I. (1975). Belief, attitude, intention and behaviour: an introduction to theory and research. In Reading, MA : Addison-Wesley (Vols. 1-578). Retrieved from https://doi.org/10.1017/CBO9781107415324.004
Flavián, C. & Guinalíu, M. (2006). Consumer trust, perceived security and privacy policy. Industrial Management & Data Systems, 106(5), 601-620. Retrieved from https://doi.org/10.1108/02635570610666403
Flavián, C., Guinalíu, M. & Torres, E. (2006). How bricks‐and‐mortar attributes affect online banking adoption. International Journal of Bank Marketing, 24(6), 406-423. Retrieved from https://doi.org/10.1108/02652320610701735
Fornell, C. & Larcker, D. F. (1981). Evaluating Structural Equation Models with Unobservable Variables and Measurement Error. Journal of Marketing Research, 18(1), 39-50. Retrieved from https://doi.org/10.1017/CBO9781107415324.004
Fred D. Davis MIS. (1989). Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Quarterly, 13(0), 319-340. Retrieved from https://doi.org/10.1016/j.cell.2017.08.036
Gbongli, K. (2017). A two-staged SEM-AHP technique for understanding and prioritizing mobile financial services perspectives adoption. European Journal of Business and Management, 9(30), 107-120.
Gbongli, K., Csordas, T. & Kissi Mireku, K. (2017). Impact of consumer multidimensional online trust-risk in adopting Togolese mobile money transfer services : structural equation modelling approach. Journal of Economics, Management and Trade, 19(2), 1-17. Retrieved from https://doi.org/10.9734/JEMT/2017/36745
Gbongli, K., Xu, Y. & Amedjonekou, K. M. (2019). Extended Technology Acceptance Model to Predict Mobile-Based Money Acceptance and Sustainability: A Multi-Analytical Structural Equation Modeling and Neural Network Approach. Sustainability, 11(13), 3639. Retrieved from https://doi.org/10.3390/su11133639
Gbongli, K., Xu, Y., Amedjonekou, K. M. & Kovács, L. (2020). Evaluation and Classification of Mobile Financial Services Sustainability Using Structural Equation Modeling and Multiple Criteria Decision-Making Methods. Sustainability, 12(4), 1288. Retrieved from https://doi.org/10.3390/su12041288
Gichuki, C. N. & Mulu-Mutuku, M. (2018). Determinants of awareness and adoption of mobile money technologies : Evidence from women micro-entrepreneurs in Kenya. Women's Studies International Forum. Retrieved from https://doi.org/10.1016/j.wsif.2017.11.013
Guitton, M. J. (2020). Cyberpsychology research and COVID-19. Computers in Human Behavior, 111, 106357. Retrieved from https://doi.org/10.1016/j.chb.2020.106357
Hair, J.F., Black, W., Babin, B., Anderson, R. & Tatham, R. (2006). Multivariate Data Analysis (6th ed.). Pearson Prentice Hall, Pearson Education, Inc., Upper Saddle River, New Jersey.
Hair, J.F., Hult, J. G. T., Ringle, C. M. & Sarstedt, M. (2017). A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM) (2nd ed). SAGE : Thousand Oaks.
Hair, Joe F., Sarstedt, M., Ringle, C. M. & Mena, J. A. (2012). An assessment of the use of partial least squares structural equation modeling in marketing research. Journal of the Academy of Marketing Science, 40(3), 414-433. Retrieved from https://doi.org/10.1007/s11747-011-0261-6
Hair, Joseph F, Black, W. C., Babin, B. J. & Anderson, R. E. (2010). Multivariate Data Analysis. In Analysis. Retrieved from https://doi.org/10.1016/j.ijpharm.2011.02.019
Hair, Joseph F, Black, W. C., Babin, B. J., Anderson, R. E. & Tatham, R. L. (2010). Multivariate data analysis : à global perspective. In Prentice Hall (7th Editio). Prentice-Hall, Inc. Upper Saddle River, NJ, USA. Retrieved from https://doi.org/10.1016/j.ijpharm.2011.02.019
Hanafizadeh, P. & Khedmatgozar, H. R. (2012). The mediating role of the dimensions of the perceived risk in the effect of customers' awareness on the adoption of Internet banking in Iran. Electronic Commerce Research, 12(2), 151-175. Retrieved from https://doi.org/10.1007/s10660-012-9090-z
Hanafizadeh, P., Behboudi, M., Abedini Koshksaray, A. & Jalilvand Shirkhani Tabar, M. (2014). Mobile-banking adoption by Iranian bank clients. Telematics and Informatics, 31(1), 62-78. Retrieved from https://doi.org/10.1016/j.tele.2012.11.001
Hashim, N. M. H. N., Pandit, A., Alam, S. S. & Manan, R. A. (2015). Why resist ? examining the impact of technological Advancement and perceived usefulness on Malaysians' switching intentions : The moderators. The Journal of Developing Areas, 49(3), 65-80. Retrieved from https://doi.org/10.1353/jda.2015.0172
Haykin, S. (1999). Neural networks : à comprehensive foundation. In The Knowledge Engineering Review.
Hong, J. I., Ng, J. D., Lederer, S. & Landay, J. A. (2004). Privacy risk models for designing privacy-sensitive ubiquitous computing systems. Proceedings of the 2004 Conference on Designing Interactive Systems Processes, Practices, Methods, and Techniques - DIS '04, 91. Retrieved from https://doi.org/10.1145/1013115.1013129
Hyndman, R. J. & Koehler, A. B. (2006). Another look at measures of forecast accuracy. International Journal of Forecasting, 22(4), 679-688. Retrieved from https://doi.org/10.1016/j.ijforecast.2006.03.001
Jacoby, J. & Kaplan, L. B. (1972). The Components of Perceived Risk. Sv, January 1972, 382-393. Retrieved from https://www.acrwebsite.org/volumes/12016/volumes/sv02/sv-02-
Kapoor, N. (2020). Ahmedabad says no to cash on delivery to stop spread of COVID-19. Retrieved from https://www.indiatvnews.com/news/india/ahmedabad-digital-payments-mandatory-no-cash-on-delivery-to-stop-covid19-616239
Kaur, S. & Arora, S. (2020). Role of perceived risk in online banking and its impact on behavioral intention : trust as a moderator. Journal of Asia Business Studies, 15(1), 1-30. Retrieved from https://doi.org/10.1108/JABS-08-2019-0252
Kelly, S. M. (2020). Dirty money : The case against using cash during the coronavirus outbreak. CNN Business, New York. Retrieved from https://www.cnn.com/2020/03/07/tech/mobile-payments-coronavirus/index.html
Kesharwani, A. & Bisht, S. S. (2012). The impact of trust and perceived risk on internet banking adoption in India : An extension of technology acceptance model. Marketing Intelligence and Planning, 30(4), 303-322. Retrieved from https://doi.org/10.1108/02652321211236923
Kim, D. J., Ferrin, D. L. & Rao, H. R. (2008). A trust-based consumer decision-making model in electronic commerce : the role of trust, perceived risk, and their antecedents. Decision Support Systems, 44(2), 544-564. Retrieved from https://doi.org/10.1016/j.dss.2007.07.001
Koenig-Lewis, N., Marquet, M., Palmer, A. & Zhao, A. L. (2015). Enjoyment and social influence : predicting mobile payment adoption. The Service Industries Journal, 35(10), 537-554. Retrieved from https://doi.org/10.1080/02642069.2015.1043278
Koenig-Lewis, N., Palmer, A. & Moll, A. (2010). Predicting young consumers' take up of mobile banking services. International Journal of Bank Marketing, 28(5), 410-432. Retrieved from https://doi.org/10.1108/02652321011064917
Kuisma, T., Laukkanen, T. & Hiltunen, M. (2007). Mapping the reasons for resistance to Internet banking : A means-end approach. International Journal of Information Management, 27(2), 75-85. Retrieved from https://doi.org/10.1016/j.ijinfomgt.2006.08.006
Lee, C., Rogers, W. A. & Braunack-Mayer, A. (2008). Social Justice and Pandemic Influenza Planning : The Role of Communication Strategies. Public Health Ethics, 1(3), 223-234. Retrieved from https://doi.org/10.1093/phe/phn031
Lee, M. C. (2009). Factors influencing the adoption of internet banking: an integration of TAM and TPB with perceived risk and perceived benefit. Electronic Commerce Research and Applications, 8(3), 130-141. Retrieved from https://doi.org/10.1016/j.elerap.2008.11.006
Lee, M. S. Y., McGoldrick, P. J., Keeling, K. A. & Doherty, J. (2003). Using ZMET to explore barriers to the adoption of 3G mobile banking services. International Journal of Retail & Distribution Management, 31(6), 340-348. Retrieved from https://doi.org/10.1108/09590550310476079
Leong, L. Y., Hew, T. S., Tan, G. W. H. & Ooi, K. B. (2013). Predicting the determinants of the NFC-enabled mobile credit card acceptance : A neural networks approach. Expert Systems with Applications, 40(14), 5604-5620. Retrieved from https://doi.org/10.1016/j.eswa.2013.04.018
Li, M., Dong, Z. Y. & Chen, X. (2012). Factors influencing consumption experience of mobile commerce. Internet Research, 22(2), 120-141. Retrieved from https://doi.org/10.1108/10662241211214539
Liang, M., Yang, X. & Ou, H. (2014). The Measurement of the Consumer Trust to O2O E-Commerce Based on Fuzzy Evaluation. 2014 Seventh International Joint Conference on Computational Sciences and Optimization, 113-116. Retrieved from https://doi.org/10.1109/CSO.2014.157
Littler, D. & Melanthiou, D. (2006). Consumer perceptions of risk and uncertainty and the implications for behaviour towards innovative retail services : The case of Internet Banking. Journal of Retailing and Consumer Services, 13(6), 431-443. Retrieved from https://doi.org/10.1016/j.jretconser.2006.02.006
Liu, X., He, M., Gao, F. & Xie, P. (2008). An empirical study of online shopping customer satisfaction in China : à holistic perspective. International Journal of Retail & Distribution Management, 36(11), 919-940. Retrieved from https://doi.org/10.1108/09590550810911683
Liébana-Cabanillas, F., Marinkovic, V., Ramos de Luna, I. & Kalinic, Z. (2018). Predicting the determinants of mobile payment acceptance : A hybrid SEM-neural network approach. Technological Forecasting and Social Change, 129, 117-130. Retrieved from https://doi.org/10.1016/j.techfore.2017.12.015
Luarn, P. & Lin, H.-H. H. (2005). Toward an understanding of the behavioral intention to use mobile banking. Computers in Human Behavior, 21(6), 873-891. Retrieved from https://doi.org/10.1016/j.chb.2004.03.003
Lucre, F. (2020). Paper money shunned as possible carrier of coronavirus. The Japan Times.
López, L. & Rodó, X. (2020). The end of social confinement and COVID-19 re-emergence risk. Nature Human Behaviour. Retrieved from https://doi.org/10.1038/s41562-020-0908-8
Martini, M., Gazzaniga, V., Bragazzi, N. L. & Barberis, I. (2019). The Spanish Influenza Pandemic: à lesson from history 100 years after 1918. Journal of Preventive Medicine and Hygiene, 60(1), E64-E67. Retrieved from https://doi.org/10.15167/2421-4248/jpmh2019.60.1.1205
Martins, C., Oliveira, T. & Popovič, A. (2014). Understanding the Internet banking adoption : A unified theory of acceptance and use of technology and perceived risk application. International Journal of Information Management, 34(1), 1-13. Retrieved from https://doi.org/10.1016/j.ijinfomgt.2013.06.002
Mitchell, V. (1999). Consumer perceived risk : conceptualisations and models. European Journal of Marketing, 33(1/2), 163-195. Retrieved from https://doi.org/10.1108/03090569910249229
Nam, T. H. & Quan, V. D. H. (2019). Multi-dimensional Analysis of Perceived Risk on Credit Card Adoption. In Studies in Computational Intelligence (Beyond Tra, pp. 606-620). Springer, Cham. Retrieved from https://doi.org/10.1007/978-3-030-04200-4_43
Narteh, B., Mahmoud, M. A. & Amoh, S. (2017). Customer behavioural intentions towards mobile money services adoption in Ghana. Service Industries Journal, 37(7-8), 426-447. Retrieved from https://doi.org/10.1080/02642069.2017.1331435
Negnevitsky, M. (2011). Artificial Intelligence 3e e-book A Guide to Intelligent Systems. In Artificial Intelligence.
Palen, L. & Dourish, P. (2003). Unpacking "privacy" for a networked world. Proceedings of the Conference of Human Factors in Computing Systems - CHI '03, 129. Retrieved from https://doi.org/10.1145/642633.642635
Pavlou, A. P. (2003). Consumer acceptance of electronic commerce : integrating trust and risk with the technology acceptance model. International Journal of Electronic Commerce, 7(3), 69-103. Retrieved from https://doi.org/10.1.1.86.7139
Pollach, I., Treiblmaier, H. & Floh, A. (2005). Online Fundraising for Environmental Nonprofit Organizations. Proceedings of the 38th Annual Hawaii International Conference on System Sciences, 178b-178b. Retrieved from https://doi.org/10.1109/HICSS.2005.470
Reuters Staff. (2020). West Africans Are Switching from Cash to Mobile Money because of COVID-19. World Economic Forum. 2020. Retrieved from https://www.weforum.org/agenda/2020/04/coronavirus-set-to-spur-mobile-money-growth-in-w-africa
Riquelme, H. E. & Rios, R. E. (2010). The moderating effect of gender in the adoption of mobile banking. International Journal of Bank Marketing, 28(5), 328-341. Retrieved from https://doi.org/10.1108/02652321011064872
Roy, S. K., Balaji, M. S., Kesharwani, A. & Sekhon, H. (2017). Predicting Internet banking adoption in India : à perceived risk perspective. Journal of Strategic Marketing, 25(5-6), 418-438. Retrieved from https://doi.org/10.1080/0965254X.2016.1148771
Sakhaei, S. F., Afshari, A. J. & Esmaili, E. (2014). The Impact Of Service Quality On Customer Satisfaction In Internet Banking. Journal of Mathematics and Computer Science, 09(01), 33-40. Retrieved from https://doi.org/10.22436/jmcs.09.01.04
Saltzer, J. H. & Schroeder, M. D. (1975). The protection of information in computer systems. Proceedings of the IEEE, 63(9), 1278-1308. Retrieved from https://doi.org/10.1109/PROC.1975.9939
Sangster, K. (2020). Banknotes may be spreading coronavirus, World Health Organisation warns. World Health Organisation. Retrieved from https://finance.yahoo.com/news/who-world-health-organisation-coronavirus-banknotes-warning-111019361.html?guce_referrer=aHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS8&guce_referrer_sig=AQAAADcTFGT17H-rKPThavsaS2UoFKHz3MsRDSqlEtXJ0YGf-d9VEGsVleL2gvKY2r7ti4Yh8S3sBn3Qlq_xY
Scott, J. E. & Walczak, S. (2009). Cognitive engagement with a multimedia ERP training tool : Assessing computer self-efficacy and technology acceptance. Information and Management, 46(4), 221-232. Retrieved from https://doi.org/10.1016/j.im.2008.10.003
Sharma, S. K. (2017). Integrating cognitive antecedents into TAM to explain mobile banking behavioral intention : A SEM-neural network modeling. Information Systems Frontiers, 1, 1-13. Retrieved from https://doi.org/10.1007/s10796-017-9775-x
Sharma, S. K., Sharma, H. & Dwivedi, Y. K. (2019). A Hybrid SEM-Neural Network Model for Predicting Determinants of Mobile Payment Services. Information Systems Management, 36(3), 243-261. Retrieved from https://doi.org/10.1080/10580530.2019.1620504
Sharma, S., Singh, G., Sharma, R., Jones, P., Kraus, S. & Dwivedi, Y. K. (2021). Digital Health Innovation : Exploring Adoption of COVID-19 Digital Contact Tracing Apps. IEEE Transactions on Engineering Management, 1-17. Retrieved from https://doi.org/10.1109/TEM.2020.3019033
Sheela, K. G. & Deepa, S. N. (2013). Review on Methods to Fix Number of Hidden Neurons in Neural Networks. Mathematical Problems in Engineering, 2013, 1-11. Retrieved from https://doi.org/10.1155/2013/425740
Shibata, K. & Ikeda, Y. (2009). Effect of number of hidden neurons on learning in large-scale layered neural networks. ICCAS-SICE 2009 - ICROS-SICE International Joint Conference 2009, Proceedings, 5008-5013. Retrieved from https://ieeexplore.ieee.org/abstract/document/5334631
Singh, S. K. & Gaur, S. S. (2018). Entrepreneurship and innovation management in emerging economies. Management Decision, 56(1), 2-5. Retrieved from https://doi.org/10.1108/MD-11-2017-1131
Smith, A. D. (2006). Barriers to accepting e‐prescribing in the USA. International Journal of Health Care Quality Assurance, 19(2), 158-180. Retrieved from https://doi.org/10.1108/09526860610651690
Sripalawat, J., Thongmak, M. & Ngramyarn, A. (2011). M-banking in metropolitan bangkok and a comparison with other countries. Journal of Computer Information Systems, 51(3), 67-76. Retrieved from https://doi.org/10.1080/08874417.2011.11645487
Stone, R. N. & Grønhaug, K. (1993). Perceived risk: further considerations for the marketing discipline. European Journal of Marketing, 27(3), 39-50. Retrieved from https://doi.org/10.1108/03090569310026637
Susanto, P., Hoque, M. E., Hashim, N. M. H. N., Shah, N. U. & Alam, M. N. A. (2020). Moderating effects of perceived risk on the determinants-outcome nexus of e-money behaviour. International Journal of Emerging Markets, ahead-of-p(ahead-of-print). Retrieved from https://doi.org/10.1108/IJOEM-05-2019-0382
Taubenberger, J. K., Kash, J. C. & Morens, D. M. (2019). The 1918 influenza pandemic: 100 years of questions answered and unanswered. Science Translational Medicine. Retrieved from https://doi.org/10.1126/scitranslmed.aau5485
Tchouassi, G. (2012). Can Mobile Phones Really Work to Extend Banking Services to the Unbanked ? Empirical Lessons from Selected Sub-Saharan Africa Countries. International Journal of Developing Societies, 1(2), 70-81. Retrieved from https://doi.org/10.11634/21681783150489
Thakur, R. & Srivastava, M. (2014). Adoption readiness, personal innovativeness, perceived risk and usage intention across customer groups for mobile payment services in India. Internet Research, 24(3), 369-392. Retrieved from https://doi.org/10.1108/IntR-12-2012-0244
Tobbin, P. (2012). Towards a model of adoption in mobile banking by the unbanked: à qualitative study. Info, 14(5), 74-88. Retrieved from https://doi.org/10.1108/14636691211256313
Trenn, S. (2008). Multilayer Perceptrons : Approximation Order and Necessary Number of Hidden Units. IEEE Transactions on Neural Networks, 19(5), 836-844. Retrieved from https://doi.org/10.1109/TNN.2007.912306
Turel, O., Serenko, A. & Bontis, N. (2007). User acceptance of wireless short messaging services : Deconstructing perceived value. Information & Management, 44(1), 63-73. Retrieved from https://doi.org/10.1016/j.im.2006.10.005
Venkatesh, Thong & Xu. (2012a). Consumer Acceptance and Use of Information Technology : Extending the Unified Theory of Acceptance and Use of Technology. MIS Quarterly, 36(1), 157. Retrieved from https://doi.org/10.2307/41410412
Venkatesh, V., Thong, J. Y. L. & Xu, X. (2012b). Consumer acceptance and use of information technology : extending the unified theory of acceptance and use of technology. MIS Quarterly, 36(1), 157-178. Retrieved from https://doi.org/10.2307/41410412
Wachanga, D. N. (2015). Ethnic differences vs nationhood in times of national crises : The role of social media and communication strategies. Journal of African Media Studies, 7(3), 281-299. Retrieved from https://doi.org/10.1386/jams.7.3.281_1
Wong, L.-W., Tan, G. W.-H., Lee, V.-H., Ooi, K.-B. & Sohal, A. (2021). Psychological and System-Related Barriers to Adopting Blockchain for Operations Management : An Artificial Neural Network Approach. IEEE Transactions on Engineering Management, 1-15. Retrieved from https://doi.org/10.1109/TEM.2021.3053359
Xu, S. & Chen, L. (2008). A novel approach for determining the optimal number of hidden layer neurons for FNN's and its application in data mining. 5th International Conference on Information Technology and Applications, ICITA 2008, 683-685. Retrieved from https://eprints.utas.edu.au/6995/
Yang, Q., Pang, C., Liu, L., Yen, D. C. & Michael Tarn, J. (2015). Exploring consumer perceived risk and trust for online payments : An empirical study in China's younger generation. Computers in Human Behavior, 50, 9-24. Retrieved from https://doi.org/10.1016/j.chb.2015.03.058
Yao, H. & Zhong, C. (2011). The analysis of influencing factors and promotion strategy for the use of mobile banking/L'analyse d'influencer des facteurs et la stratégie de promotion pour l'usage des opérations bancaires mobiles. Canadian Social Science, 7(2), 60-63. Retrieved from http://search.proquest.com/docview/873571634?accountid=32277
Yao, J., Tan, C. L. & Poh, H.-L. (1999). Neural Networks for Technical Analysis: A Study on KLCI. International Journal of Theoretical and Applied Finance, 02(02), 221-241. Retrieved from https://doi.org/10.1142/S0219024999000145
Zhao, A. L., Hanmer-Lloyd, S., Ward, P. & Goode, M. M. H. (2008). Perceived risk and Chinese consumers' internet banking services adoption. International Journal of Bank Marketing, 26(7), 505-525. Retrieved from https://doi.org/10.1108/02652320810913864
Zikmund, G. W. & Scott, E. J. (1974). A Multivariate Analysis of Perceived Risk Self-Confidence and Information Sources. In in NA - Advances in Consumer Research Volume 01 (eds. Scott, pp. 406-416). Retrieved from https://www.acrwebsite.org/volumes/5673/volumes/v01/NA-01
De Kerviler, G., Demoulin, N. T. M. & Zidda, P. (2016). Adoption of in-store mobile payment : are perceived risk and convenience the only drivers ? Journal of Retailing and Consumer Services, 31, 334-344. Retrieved from https://doi.org/10.1016/j.jretconser.2016.04.011
APPENDIX
Conceptual framework of variables
|
Items |
Measurement scales |
|
Perceived privacy risk (PPR) Cheung
and Lee (2001), Flavián
and Guinalíu (2006) |
|
|
PPR1 |
I think subscribing to mobile money service (MMS)
increases the likelihood of receiving spam/ spam SMS |
|
PPR2 |
I think MMS providers could provide my personal
information to other companies without my consent |
|
PPR3 |
I think mobile money service providers will send SMS
advertisement without the user's consent |
|
PPR4 |
I think MMS providers endanger my privacy by using
my personal information without my permission |
|
Perceived time risk (TIR) Nam and
Quan (2019), Yang et
al. (2015) |
|
|
TIR1 |
I worry that it will cost me much time to access
mobile money services. |
|
TIR2 |
It takes time to perform transactions using mobile
money service |
|
TIR3 |
It takes time to solve problems with mobile money
service |
|
TIR4 |
I worry that it will cost me much time to confirm my
ID and other details for mobile money transactions |
|
Perceived security risk (SER) Yang et
al. (2015),
(Featherman and Pavlou (2003)) |
|
|
SER1 |
I worry that a third party will steal the
transaction information. |
|
SER2 |
I worry that a third party will use my account
information to perform an illegal transaction. |
|
SER3 |
I worry that a third party can withdraw the money I
send via mobile money. |
|
SER4 |
I worry that the money I send through mobile money
will not reach the intended recipient. |
|
Perceived monetary risk (MOR) Kuisma
et al. (2007), Fain and
Roberts (1997) |
|
|
MOR1 |
The use of mobile money services is economical |
|
MOR2 |
In my opinion, using mobile money service saves cost |
|
MOR3 |
The use of mobile money services increases my
ability to control my financial matters by myself |
|
Perceived overall risk (POR) Featherman and Pavlou (2003), Roy et
al. (2017) |
|
|
POR1 |
Considering all sorts of factors combined, using
mobile money service exposes me to a comprehensive risk |
|
POR2 |
The mobile money service provider may not deliver
the expected standard of service |
|
POR3 |
I may not be able to access my account because of a
poor network connection |
|
POR4 |
Using mobile money service for a financial
transaction would be risky |
|
POR5 |
I may not get financial advantages as suggested by
the mobile money service provider |
|
Behavioral intention to use the system (BI) Fred D.
Davis MIS. (1989), Davis et
al. (1989), Venkatesh et al. (2012b) |
|
|
BI1 |
I will use/continue using mobile payment services in
the future |
|
BI2 |
I will always try to use mobile money service in my
daily life |
|
BI3 |
I will likely use/continue using mobile payment
services in the future |
|
BI4 |
Given a chance, I predict I will use/continue using
mobile payment services in the future |
 This work is licensed under a: Creative Commons Attribution 4.0 International License
This work is licensed under a: Creative Commons Attribution 4.0 International License
© Granthaalayah 2014-2022. All Rights Reserved.